news
Emotet is disrupted, but the malware it installed lives on
In this News Article
Jump to
The successful takedown of the Emotet C2 infrastructure announced January 27th 2021 is no small accomplishment, both from a technical point of view and for the larger safety and security of the internet as a whole. However, Emotet often drops other malware which can still work even though Emotet no longer does. For those infected with Emotet, a significant challenge remains.
What was Emotet?
Emotet was one of the most dangerous, destructive, and prolific variations of malware active on the internet recently. Over time it became a monetized platform for threat actors to run malicious campaigns on a pay-per-install (PPI) model, allowing theft of sensitive data and ransom extortion. To give you an idea of its scope, the number of Microsoft Windows computers currently compromised by Emotet is estimated to be over one million.
Emotet began its career in 2014 as a banking trojan and evolved over the years into a "malware as a service" infrastructure that gave access to exploited networks to anyone that could pay the asking price. On consumer PCs, Emotet acted as an information and password stealer. It also contained a spam module that allowed Emotet to spread laterally using email as a vector, using malicious links or attachments.
It was sending tens of thousands of malware-laden emails every day through accounts it had previously compromised, posing as account detail alerts, information about Covid, shipping notifications and other themes designed to invoke user interaction. One important strategy was using email thread hijacking: inserting poisoned emails into existing conversations to fool the recipients into opening the bait.
On corporate networks that are part of a Windows domain, Emotet performed reconnaissance and then acted as a dropper for additional malware on the victim's machines. Once the threat actors gathered enough information and gained access to high-privileged accounts (such as domain administrator accounts), the attackers encrypted corporate networks using ransomware. Their targets included - among others - private individuals, companies, government institutions, and healthcare providers, including hospitals: a significant percentage of the malware affecting computer networks in the healthcare industry are trojans. The most common of them is Emotet.
Emotet is distrupted, but the malware it installed lives on.
Emotet could be seen as a springboard to deliver other malware families. The ultimate goal of these is often to steal financial data in the broadest sense of the word and encrypt corporate networks. The latter often causes complete work stoppage, while enabling criminals to extort ransom from the network owners to regain control. If an Emotet infection is present, it is safe to assume that one or more computers are infected with at least one - and probably several - of these malicious programs as the following chart illustrates perfectly:
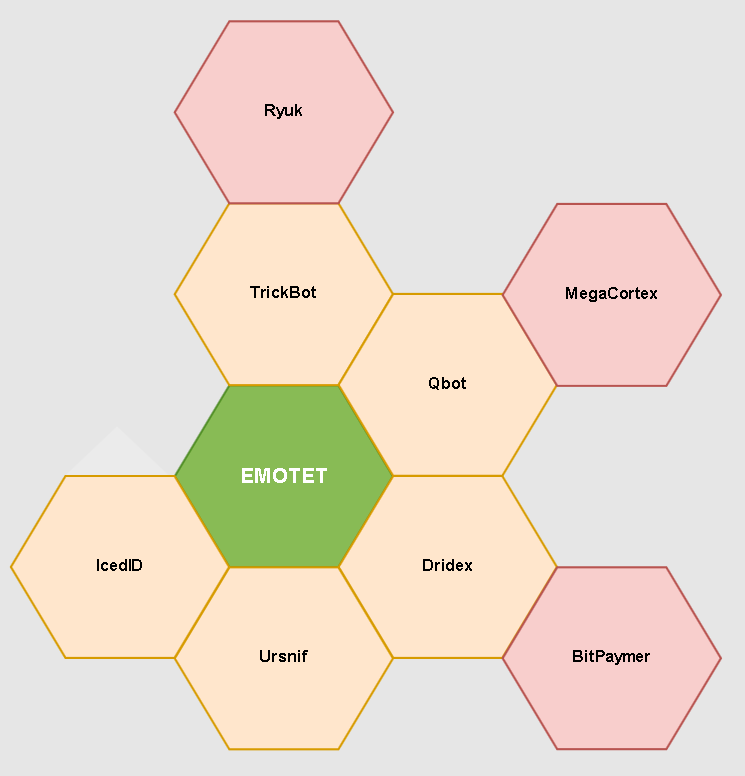
Emotet infections often lead to further malware being deployed. Graph via @pollo290987
The most common malware families deployed through Emotet are:* IcedID: A banking trojan that injects itself into browsers, intercepting communications with banks, e-commerce and payment card providers.
- Ursnif: Steals password and credentials, banking and financial information.
- Dridex: Yet another malware family specialized in stealing banking credentials and other passwords. Machines infected with Dridex may be infected with Bitpaymer ransomware later.
- Qbot: primarily a banking trojan and password stealer. Qbot infections have been known to deliver Megacortex, another variation of the ransomware family.
- TrickBot: A trojan that attempts to steal customer access credentials for their bank accounts, which is usually paired with Ryuk: An encryption trojan - also known as ransomware. It encrypts data and locks out the legitimate owners. This is then used to extort the owners to regain access, often for significant amounts of money.
Found Emotet? Keep looking for more
It is crtitical to not get complacent as a result of the Emotet takedown - the dropped malware from it is still present, and is capable of causing extensive damage once exploited by other threat actors. In short:
- All computers and servers should be thoroughly scanned with an up to date anti-virus/malware.
- All administration, user, FTP & CMS passwords should be changed.
- Logging should be enabled and regularly analyzed for anomalous traffic.
- End user education about opening attachments and links is always a good idea.
What does Spamhaus do?
Spamhaus is actively helping remediate existing Emotet malware distribution sites that are still out there. We also notify end users, networks and national CERTs (through our CERT portal) about Emotet infections within their constituency.
Stay alert, stay safe! Sadly, the next advancement of malware is usually just around the corner.


