About the Data
Utilizing IP and domain reputation data at the DNS-level and your network perimeter to block and drop connections to IPs, ASNs, and domains.
How can reputation data be used at the DNS level?
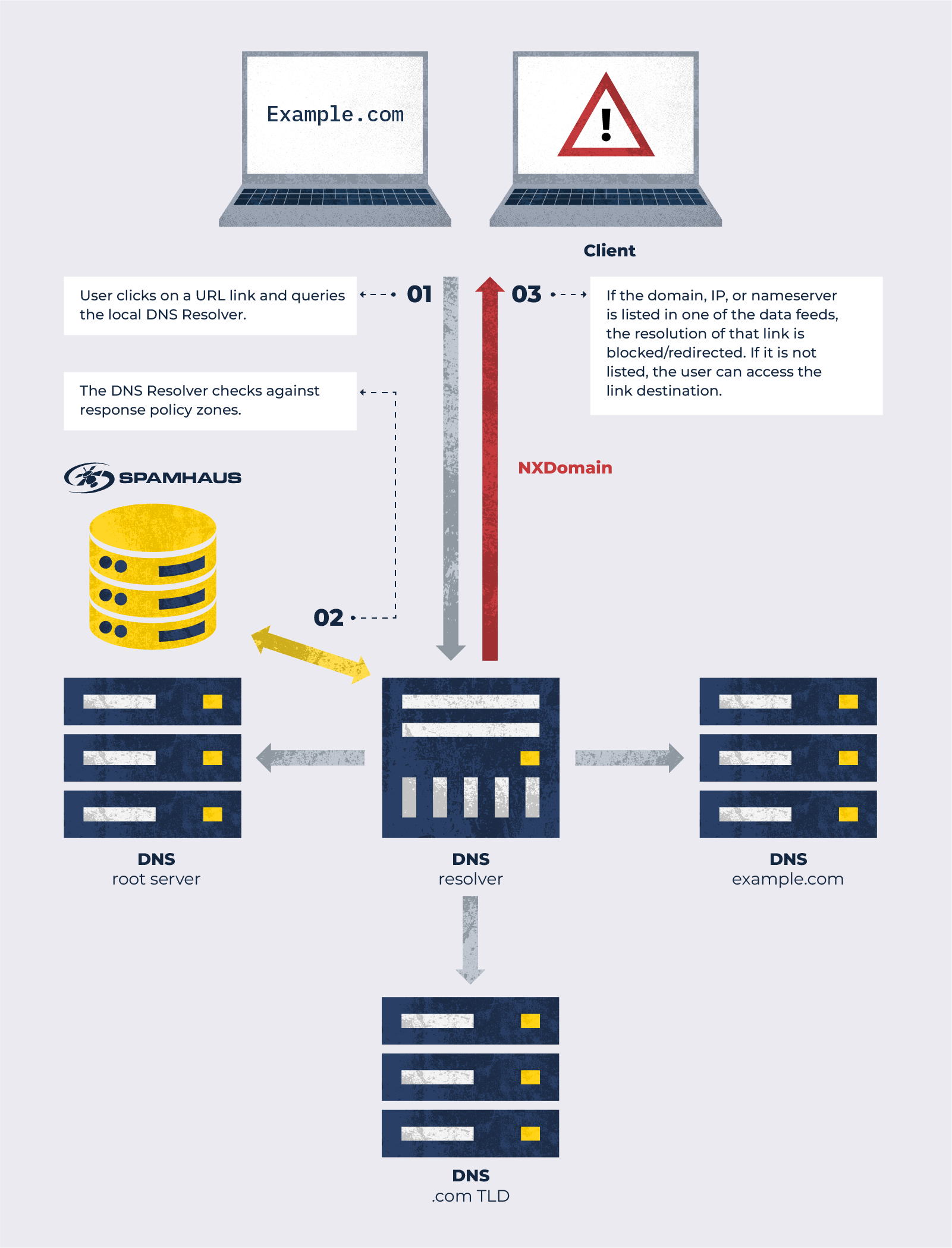
Our partner, Spamhaus Technology, uses the reputation data we produce to create response policy zones (RPZ), which can be applied to mainstream DNS resolvers such as BIND and Unbound. This ensures that users within your network who try to connect to potentially harmful websites and URLs are automatically blocked. To better understand RPZs and DNS Firewall, read this beginner’s guide.
How response policy zones work:
How can reputation data be used for perimeter protection?
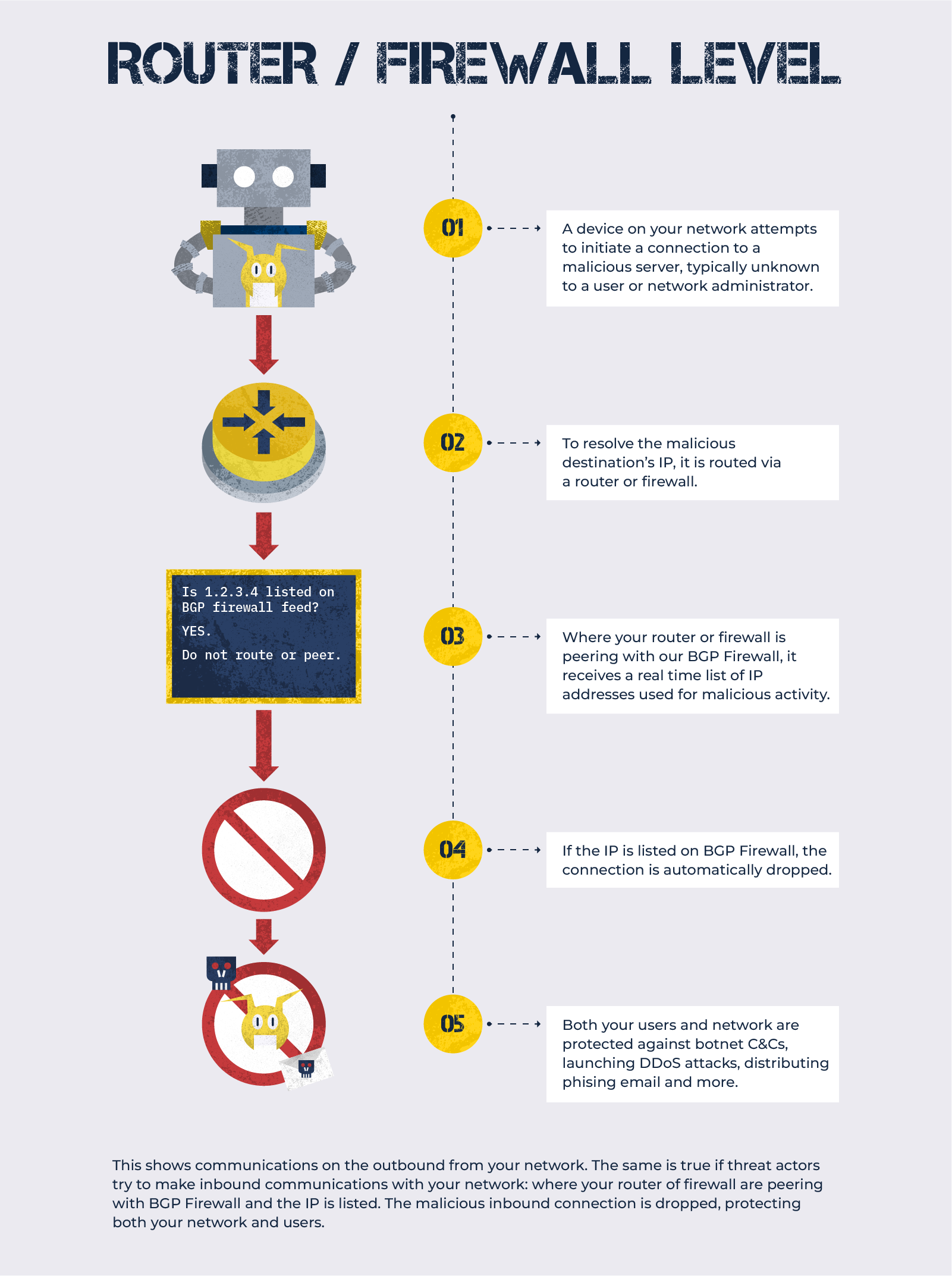
By applying “ communities” at your network edge via firewalls or BGP routers, you can block the worst of the worst (attempted) connections. Spamhaus Project provides DROP text files for free for use with existing firewalls.
For a more commercially-focused solution, which includes communities listing abused and dedicated botnet command and controllers (C&Cs), we make data available via our partner Spamhaus Technology. Find out more about BGP Firewall.
What data can I access for network protection?
DROP IPv4
IPv4 netblocks, respectively, that are "hijacked" or leased by professional spam or cyber-crime operations, directly allocated by an established Regional Internet Registry (RIR) or National Internet Registry (NIR)
DROP IPv6
IPv6 netblocks, respectively, that are "hijacked" or leased by professional spam or cyber-crime operations, directly allocated by an established Regional Internet Registry (RIR) or National Internet Registry (NIR)
ASN DROP
Autonomous System Numbers (ASNs) controlled by spammers or cyber criminals, as well as "hijacked" ASNs.