news
Bulletproof hosting – there’s a new kid in town
In this News Article
- Introduction
- The preferred choice of cybercriminals
- Taking a stand against bulletproof hosting companies
- Current challenges facing traditional bulletproof hosting companies
- New modus operandi of a bulletproof hosting operation
- What operations are running on this hosting service?
- What are the benefits for cybercriminals of using this new bulletproof hosting set-up?
- How to combat this new threat?
Jump to
Introduction
Our researchers have uncovered a new breed of "bulletproof" hosting. Worryingly, the set-up for cybercriminals is more cost-effective, less risky, and provides greater agility compared with that of 'conventional' bulletproof hosting, making it easier for them to host all kinds of badness. Here's what you need to know...
The preferred choice of cybercriminals
For a long time, “bulletproof” hosting was a favorite place for spammers, phishers, botnet operators, and malware authors to host their infrastructure on.
Why? Well, unlike other hosting providers, bulletproof hosting companies do not act on abuse reports. As you can imagine, this is an attractive proposition for bad actors; they can rest easy, comfortable in the knowledge that their malicious infrastructure will stay online without fear of it being taken down.
Taking a stand against bulletproof hosting companies
Since its founding days, well over 2 decades ago, The Spamhaus Project has identified dozens of bulletproof hosting companies, most of which were subsequently shut-down, negatively impacting the operations of cybercriminals across the globe. Some famous examples include McColo, 3FN and CB3Rob (also known as “Cyberbunker"). That last disconnect resulted in one of the most severe DDoS attacks ever seen in history, targeting ‘spamhaus.org.' More recently Maxided and 'Cyberbunker 2.0' were taken offline by various authorities.
Current challenges facing traditional bulletproof hosting companies
Recently, running a bulletproof hosting company has become somewhat more difficult. There are several reasons for this, including:
- Internet and transit providers do not wish to get associated with these types of illegal operations. If they route or peer with a network that is known to provide bulletproof hosting, these Internet & transit providers are viewed in a bad light, damaging their reputation. Internet and transit providers don’t wish to associate with illicit network operations. Routing bulletproof hosting networks can affect the upstream’s reputation and connectivity, and financial transactions with unscrupulous operations are uncertain. Connections on the internet rely on trust relationships, and poor reputation removes that trust.
- Spamhaus publishes a ‘Don’t Route or Peer’ (DROP) list, which contains netblocks and, more recently, AS numbers that are leased to identified spammers or cybercrime operators. This list is utilized by many Internet Service Providers (ISPs) who consult the DROP list before they announce or peer with a new AS/prefix. As a result, miscreants are finding it increasingly difficult to have an ISP announce their netblock.
- Over the past few years, anonymization networks such as Tor, have become increasingly popular. The advantages provided by such networks, such as providing threat actors with full anonymity, alongside immunity against takedown attempts, has led some to move their operations away from bulletproof hosting companies onto the dark web.
It is important to note, however, that there are a handful of disadvantages to moving infrastructure, such as botnet C&C servers, onto anonymization services:
Malware needs to be able to communicate through the anonymization network
These networks are inclined to be slow and unreliable
Taking all the above into consideration, it’s safe to say that from a cybercriminal’s perspective, running a bulletproof hosting company isn’t always easy. But it appears there’s a new kid on the block! Earlier this year, we identified a new hosting provider, selling its bulletproof hosting services on the dark web.
New modus operandi of a bulletproof hosting operation
Our investigations have shown that this latest bulletproof hosting provider operates with a new “modus operandi." One that is entirely different from that which we have observed previously, with traditional, bulletproof hosting companies.
To date, these types of companies have operated their own netblocks, and occasionally even their own ASs. This new operation, however, is renting virtual private servers (VPSs) at legitimate hosting providers using stolen or fake identities. They ask their customers to point their domain names to the newly registered VPSs. What then takes place is that these front-end servers act as reverse-proxy servers, forwarding the incoming traffic towards a chain of reverse proxy servers to the final backend.
Almost without exception the domain names that are pointing to these newly registered VPSs have the following commonalities:
- The domains usually have 3-4 A records with a public Time to Live (TTL) of 600 seconds
- The domains all use the Chinese DNS operator DNSpod (Tencent) for DNS resolution ([a-c].dnspod.com)
- All A records have a Nginx running on port 80 and port 443
What operations are running on this hosting service?
This year we have seen a large variety of cybercrime operations being hosted this way, including:
- Carding and hacker forums
- Spammer sites
- Phishing sites
- Malware distribution sites
- Botnet C&Cs
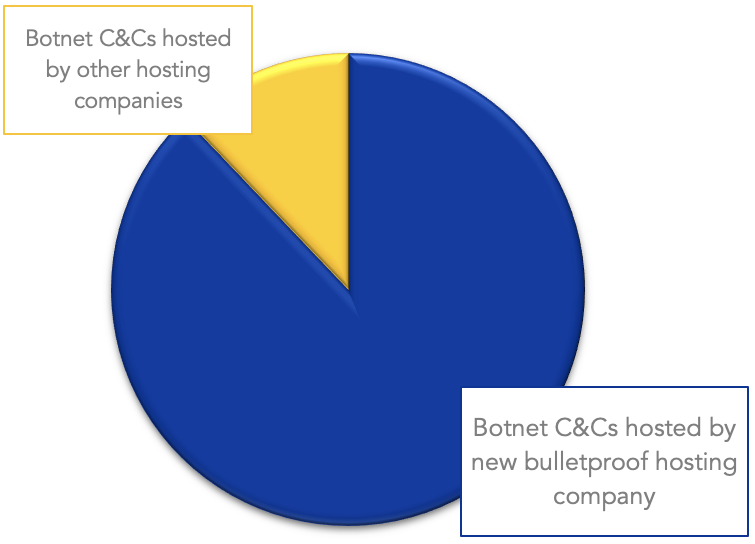
As stated above, the actual hosting is done on virtual servers across many different networks and providers. Most of these providers are located in Russia, and all share the following factors:
- They are very cheap
- They accept payments from the Russian payment service provider WebMoney
- They have a weak or even nonexistent customer verification/vetting process. This allows threat actors to sign-up for a new VPS without going through a process that vets both their identity and order, which in turn exposes these cheap VPS providers to a large amount of abuse.
From September 2019 to the third week of december 2019, Spamhaus has identified a total of 4,117 botnet C&Cs. Of which, 3,620 were hosted on this new bulletproof hosting outfit, meaning that in terms of 'market share' related to botnet C&C activity, this organization is hosting the vast majority of them.
The table below lists the top hosting providers that are being (ab)used by this new bulletproof hosting company:
| # of botnet C&Cs | Hosting provider | Country |
|---|---|---|
| 325 | simplecloud.ru | Russia |
| 283 | reg.ru | Russia |
| 239 | ispserver.com | Russia |
| 215 | mtw.ru | Russia |
| 199 | timeweb.ru | Russia |
| 170 | marosnet.ru | Russia |
| 164 | spacenet.ru | Russia |
| 135 | melbicom.net | Russia |
| 125 | mchot.ru | Russia |
| 117 | netangels.ru | Russia |
| 117 | greenvps.net | Russia |
| 109 | nethost.com.ua | Ukraine |
| 97 | itos.biz | Russia |
| 79 | confortel.pro | Russia |
| 65 | dhub.ru | Russia |
| 64 | adminvps.ru | Russia |
| 60 | ruvds.com | Russia |
| 58 | server-panel.net | Ukraine |
| 52 | selectel.ru | Russia |
| 46 | galadydata.ru | Russia |
What are the benefits for cybercriminals of using this new bulletproof hosting set-up?
Running a bulletproof hosting company this way comes with various advantages to cybercriminals, compared to the traditional model:
- Minimal threat from law enforcement - A vast amount of these VPS providers are located in Russia and hence outside the reach of western law enforcement agencies.
- Minimal cost - These VPS providers are all very cheap, which is a positive given the fact that a single VPS generally only stays active between a couple of hours to a maximum of a couple of days.
- Agility - Despite most of these VPS providers quickly shutting down the VPSs being used for malicious purposes, this bulletproof hosting company can quickly change the A record of the customer’s domain name (even in an automated way using DNSPod’s API).
- Minimum impact on operations - All of these domain names are using multiple A records, therefore shutting down just 1-2 of them will have almost no effect on the cybercrime operation, as others remain active.
How to combat this new threat?
This new modus operandi works only so long as long as there are (cheap) hosting providers that have a weak or non-existent customer vetting/verification service. We have published guidelines outlining how hosting providers should vet their new customers to battle fraudulent sign-ups. Also, domain registrars must adopt a similar process to vet new domain registrants. Furthermore, registrars need to shut down registrants and resellers that have a high volume of fraudulent domain registrations.
Spamhaus users are protected from spammer, phishing, and malware sites, as well as botnet C&Cs hosted by this bulletproof organization, by using the following data feeds:
- Spamhaus Don’t Route Or Peer Lists (DROP)
- Spamhaus Domain Block List (DBL)
- Spamhaus Botnet Controller List (BCL)
It’s no great surprise that we are witnessing a change in the set-up of bulletproof hosting companies; the threat landscape is constantly evolving in the ‘cat & mouse’ game that is played out between those who wish to protect the Internet and those who wish to make illegal gains from it. However, this does, once again, highlight the fact that EVERYONE who has a stake in the Internet needs to responsibly play their part in keeping it a safe environment.