Frequently Asked Questions relating to Spamhaus data
Frequently asked questions relating to our data and research.Categories
- Botnet Controller (BCL)
- Commercial Data
- Consumer
- CSS Blocklist (CSS)
- DNSBL Usage
- Domain Blocklist (DBL)
- DROP
- Exploits Blocklist (XBL)
- General Definitions
- General Questions
- Hacked - General Help
- Hash Blocklist (HBL)
- ISP General Questions
- Legal Questions
- Malware Questions
- Marketing Email
- Media Enquiries
- Online Scams
- Organization
- Policy Blocklist (PBL)
- Port 25 General Questions
- Reputation Statistics
- ROKSO
- Spamhaus Blocklist (SBL)
- Zero Reputation Domain (ZRD)
Categories
Exploits Blocklist (XBL)
The Spamhaus Exploits Blocklist (XBL) is a realtime database of IP addresses used by hijacked devices compromised by 3rd party exploits.
The range of exploits we track and list changes constantly to reflect the real-world threat map.
The IP was listed because we have compelling evidence that suggests that the machine using the IP or one or more devices behind it are insecure, compromised, or infected.
If it’s a spambot: to stop the abuse immediately, close port 25 on the router or firewall, and restrict port 25 access to known email servers.
- NOTE: Closing port 25 will only prevent the abusive connections from leaving your network. If the problem is (for example) an infected mobile phone, when it moves to another insecure network, it will resume its activity without restriction.
To find and eliminate the source of the problem, please see the our FAQs:
Is the IP a NAT gateway, firewall or router?
- The infected devices are usually computers or other devices (such as mobile phones) behind the router, but in some cases it can also be the router itself.
- Please consult the documentation or manufacturer of your router or firewall to see how to ensure that the device is properly secured, and make sure its software is up to date.
General considerations:
- Microsoft Windows operating systems: any or all of the following free tools may help: Windows Defender, Malwarebytes, Norton Power Eraser, CCleaner, or McAfee Stinger.
- Make sure that Windows is running the most up-to-date and patched version of the available operating system.
- All operating systems: Check tool-bars, extensions and plug-ins on each browser for anything you don’t recognize. Look for for “free” VPNs or other heavily-monetized apps.
- Calling your ISP, IT department, or taking your suspect machine(s) to a competent tech support service might also be useful.
The IP is being re-listed because the detected problem has not been corrected, and we continue to see activity that indicates that the IP or one or more devices behind it are insecure, compromised, or infected.
Please see the previous entry for possible solutions.
In this situation is it probable that the IP had been blocked by XBL, but has been recently removed. If that is the case:
- Not all networks sync updates from us at the same speed. Please allow 24 hours to pass before opening a new ticket.
- If an IP was listed on the XBL, it happened because XBL received either spam or a virus directly from the IP. If the problem that caused the listing is not resolved, the IP will re-list the next time it makes a connection to us.
More often than not, with UNIX like operating systems, the problem is not malware as in “virus,” it is security: systems that are deployed and forgotten will get compromised.
Anything visible on the Internet will be attacked the moment it becomes visible. It is the owners’ responsibility to secure their systems, keep them up to date, and in a worst case scenario be prepared to to delete and rebuild them if they are compromised.
Web servers are a particulary popular target, and applications like WordPress, Joomla and Drupal must be kept updated and patched at all times. Plugins are especially vulnerable. Many compromises are caused by poorly written PHP, and random scripts downloaded from the Internet.
The next most common issue is, it is not the device itself, but something behind it that is compromised. This usually means firewalls, NAT gateways and VPN concentrators, guest Wi-Fi networks, etc.
- Firewalls should be configured on a basis of “open only the ports you need” rather than “close the ports you do not.”
- NAT gateways should have firewall rules applied.
- VPN Concentrators should not allow VPN clients to access the internet, only the intranet. Many times, misconfigured VPNs mean that the server has been listed because the remote client is infected with malware.
- Guest Wi-Fi should never be allowed to share IP addresses with services that matter and permitting insecure protocols such as SMTP can and will result in problems.
Misconfigured Plesk hosts can have unexpected outcomes – the behavior of such a host closely mimics the behavior of a certain type of spambot.
Plesk’s online guide describes the “Outgoing mail mode” option and its three settings:
- Send from domain IP addresses:
By default, mail from each domain is sent from the domain’s IP address. The host name used in the SMTP greeting is the Plesk server host name specified in Tools & Settings > Server Settings. Selecting this option may result in mail sent from some or all domains being marked as spam if the Plesk server host name fails to resolve properly, or if the domain’s IP is different from the one to which the Plesk server host name resolves.
This option works best if it is required to have a single IP address on the Plesk server.
- Send from domain IP addresses and use domain names in SMTP greeting
If selected, Plesk changes the mail server configuration so that the SMTP greeting contains the name of the domain from which the email message is sent.
Warning: Selecting this option may result in mail sent from some or all domains being marked as spam if the destination mail server uses Spamhaus XBL and more than one domain on the Plesk server uses the same IP address.
In addition, selecting this option on Plesk servers hosting a large (more than 100) number of domains will likely result in significantly increased server load.
This option works best if a dedicated IP address is allocated to every domain hosted on the Plesk server, and the number of domains hosted on the server is not very large.
- Send from the specified IP adresses:
If it is required to use certain IPv4 and IPv6 addresses for all outgoing mail.
If None is selected, outgoing mail will not be sent.
The first setting is shown as ‘enabled’ circled in red in the screen shot below:
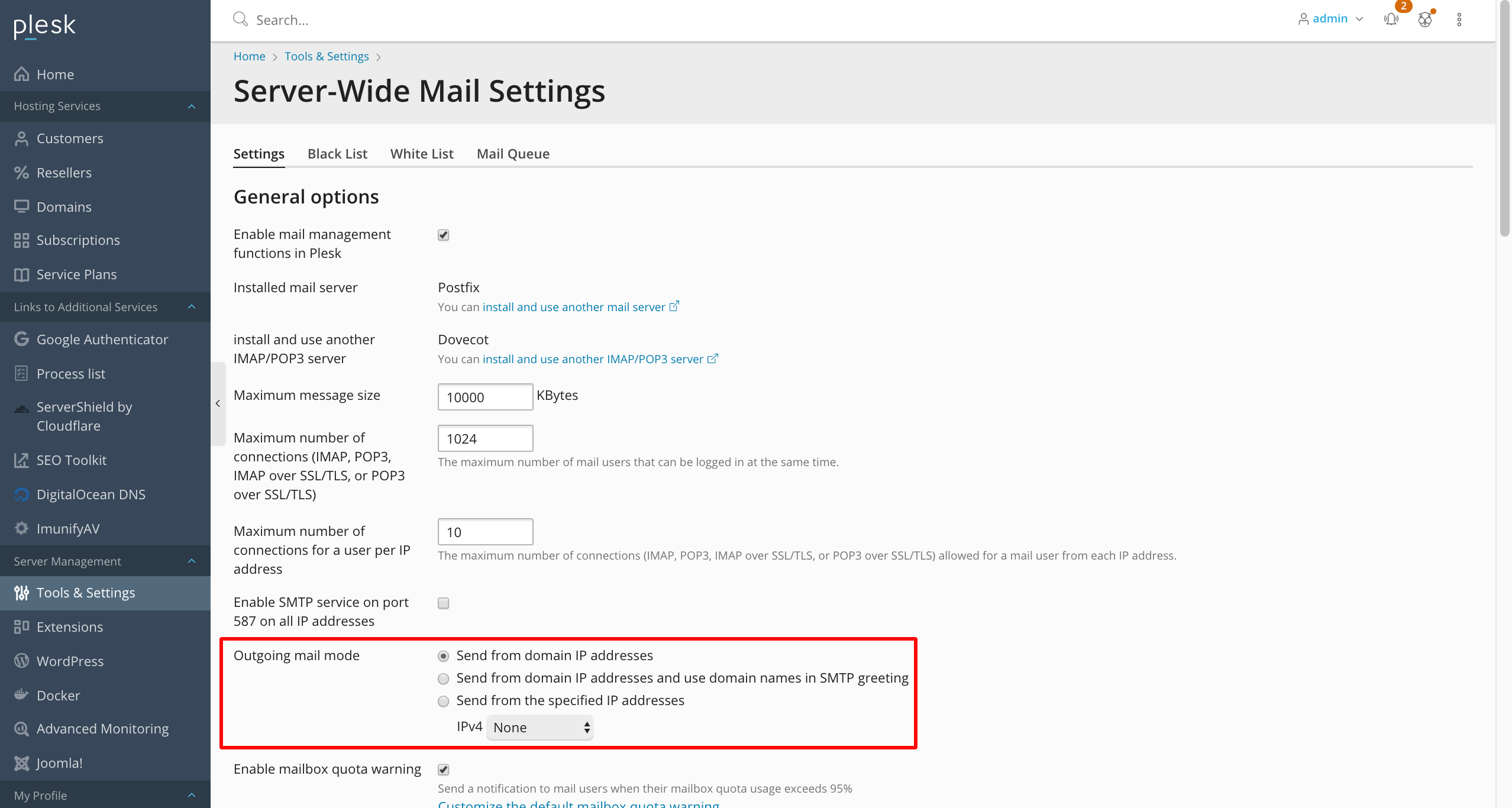
We recommend you use the first or third option in virtually all cases.
The second option, “send from domain IP addresses and use domain names in SMTP greeting” can lead to reputational and XBL issues, and should be used with extreme care:
- Many Plesk installations are unable to bind to different IP addresses to send email on behalf of each hosted domain. This is especially true if the web server uses a single IP address to host multiple domains by “virtual host” – there are no other addresses to bind to, so, it’s using the same IP address all the time.
- The “send from domain IP addresses and use domain names in SMTP greeting” option should only be used if you’re certain your installation can successfully bind to specific outbound IP addresses, and that each IP address will only be used for at most 2-3 different domains.
If you are using cPanel, and need to set or change a HELO/EHLO value, this cPanel support article will show how it is done.
If you are using Direct Admin, and need to set or change a HELO/EHLO value, this Direct Admin web control panel support article will show how it is done.
The DNS return code (127.0.0.?) denotes the source of the data in the XBL or the SBL-XBL and ZEN combined zones. Only one code is currently used by XBL:
127.0.0.4 – XBL
127.0.0.5 and 127.0.0.6 are no longer in use at this time. 127.0.0.5, 127.0.0.6 and 127.0.0.7 remain allocated to XBL for possible future use.
Providers should not use the XBL to block their own users, or to deny access to web-forums, journals or blogs.
- If the same hosts are used for both incoming email and outgoing (smarthosted) email, connections using SMTP authentication should be exempted from XBL checks.
- End users are often on dynamic IP addresses: a user may be assigned an IP address from their provider that is listed in the XBL because of the situation of a previous user of that IP address.
- The XBL can be used to alert an ISP’s security department when a user’s IP is in the XBL, but should only be used as an “informational” alert.
The SBL DNS zone is rebuilt and reloaded every 5 minutes, 24/7, to ensure that new spam problems are swiftly blocked and that fixed problems are swiftly removed.
- To ensure high redundancy, Spamhaus has over 80 public DNSBL mirror servers located around the world.
- All respond in realtime to public queries.
No. The XBL is an automatic system whose detectors need to receive connections (spam, malware, viruses, etc.) directly from the IP address involved. There is no way for third parties to add IP addresses to the XBL.
We have developed our datasets with the final goal of being the most compatible with existing software. The two biggest open source antispam projects are SpamAssassin and Rspamd.
To show the best way to use our data with these products, we have created two dedicated Github projects. The projects contain instructions, rulesets, and code to make the best out of our DQS product.
XBL lists /64 subnets of IPv6 addresses.
- IPv6: XBL lists “/64” or larger CIDR blocks.
- A very large number of spam-emitting IPv6 addresses in different /64 blocks within the same network could cause listings to extend to larger blocks.
- Without such extensions/aggregations, the IPv6 zone size could become unworkably large.
- Various strategies used by spammers to game the system are made much more difficult by the use of aggregated blocks rather than single “/128” IPs.
A “/64” is the industry standard for the smallest IPv6 allocation to individual customers, even for home-uses like cable, DSL or wireless.
- For ISPs which follow standard industry practices, XBL IPv6 listings will only affect a single customer.
- The “/64” choice has RFC4291 as its origin and it is further discussed in RFC6177
- More technical reasons for choosing /64 customer assignments, at minimum, are discussed on Slash64.net, and in M3AAWG document “Policy Issues for Receiving Email in a World with IPv6 Hosts.”
IPV6 allocation information quoted from the Regional Internet Registries (RIRs) documentation:
6.4.1. Assignment address space size: + “Assignments are to be made using the following guidelines: - /48 in the general case, except for very large subscribers. - /64 when it is known that one and only one subnet is needed by design. - /128 when it is absolutely known that one and only one device is connecting.”
10.1. LIR assignments to end sites: + “An LIR can assign a /64 to /48 to an end site customer network based on their requirements. The following guidelines may be useful: - /64 where it is known that only one subnet is required. - /56 for small sites where it is expected only a few subnets will be required within the next two years. Subscribers can receive a /56 when connecting through on-demand or always-on connections such as small office and home office enterprises. - /48 for larger sites, or if an end site is expected to grow into a large network.”
ARIN, Your First IPv6 Request
- Step 2: Determine Your Block Size:
“IPv6 block size is based on the number and size of subnets to be assigned to customers, not on the number of IP addresses required by customers. ISPs will typically assign one subnet (/48 or smaller) to each customer. The default /32 minimum allocation is sufficient for many ISPs since it contains 65,536 /48 subnets to assign to customers. ISPs may also opt to request a smaller /36 allocation.”
LACNIC, IPv6 Address Allocation and Assignment Policies
- 4.5.3.1 – Assignment address space size:
“End sites or users must be assigned a prefix that is a multiple of “n” /64’s which must be enough to meet their current and planned needs, considering existing protocols and future possibilities and thus avoiding possible renumbering scenarios.” - The size of the prefix to be assigned is an operational decision of the LIR/ISP, although the selection of /48s is recommended for simpler and more functional infrastructure for all the endpoints of the network. - Persistent prefix assignments are recommended to avoid undesired failures. - Using a /64 prefix for point-to-point with GUAs is recommended.”
- 4.2. Prefix assignment options:
“A single network at a customer site will be a /64. At present, RIR policies permit assignment of a /48 per site, so the possible options when choosing a prefix size to delegate are /48, /52, /56, /60 and /64. However, /64 is not sustainable, it doesn’t allow customer subnetting, and it doesn’t follow IETF recommendations of “at least” multiple /64s per customer. Moreover, future work within the IETF and recommendations from RFC 7934 (section 6) allow the assignment of a /64 to a single interface (https://tools.ietf.org/html/draft-ietf-v6ops-unique-ipv6-prefix-per-host-07).”
RIPE, IPv6 Address Allocation and Assignment Policy
- 5.4.1 Assignment address space size:
“End Users are assigned an End Site assignment from their LIR or ISP. The size of the assignment is a local decision for the LIR or ISP to make, using a value of “n” x /64. Section 4.2 of ripe-690 provides guidelines about this.”
Customers of providers that assign different customers within the same /64 block should contact their provider’s support, ask for a dedicated /64 assignment, and move mail service to a non-shared /64 range.
NOTE: Linode customers should read this document, then access the panel, add a /64 prefix routed range, pick up an address within that range and configure their MTA to use that address, rather than the /128 SLAAC address.
- IPv6: XBL lists “/64” or larger CIDR blocks.
Here are some basic general security best practices:
For home networks & end users:
- Update operating systems and software on all computers and devices.
- Update your anti-virus/anti-malware programs, and run full scans on every device that is possible.
- Any smart devices that are not needed should be disconnected from the network immediately.
For business/office/enterprise environments:
- Update operating systems and software on all computers and devices.
- Update your anti-virus/anti-malware programs, and run full scans on every device that is possible.
- Verify router and firewall configurations and ensure the firmware is the most recent version.
- Disable any unnecessary external access to your router & network, and appropriately secure any necessary external access procedures.
- Monitoring and reviewing network traffic for unusual patterns or destination ports can be very useful.
- Consider investing in a host-based IDS or an enterprise anti-malware solution, and update it frequently.
“Network Address Translation” (NAT) is used to “map” the private, non-routable IP addresses of individual computers on a local network to a single public-facing IP address (the “NAT’s address”) on the Internet.
- Many providers use this to remap their end-consumer IP addresses to the Internet.
- Many small networks (small office and home networks) use NAT to remap their home or office machines through a cable modem or firewall to the Internet.
A NAT firewall, router or gateway is a piece of equipment or software that makes the bridge between a local network and the Internet.
- It makes all of the connections appear to be from the NAT address, not the local address of the LAN computer.
IMPORTANT NOTE: If you are running your own wireless router/firewall, it is often possible for “unwanted guests” to sneak onto your network (either accidentally or deliberately) and emit malicious or unwanted traffic through your Internet connection – as well as have full access to your private network! It is critical that you take steps to protect your wireless connection.
What’s significant about NATs?
Most modern malware and spam-sending exploits have their own built-in SMTP clients, and will attempt to send directly out from the infected machine.
- They DO NOT go through the infected network’s mail server, and DO NOT leave mail server logs of any kind: This means that the virus will establish a SMTP port 25 connection directly to the recipient mail server.
- Anti-spam and anti-malware scanners on your mail servers will not find these infections, because the spam is not going through the mail servers.
Since all malware and spam-sending exploits forge headers, the only information we know is the originating IP address – which is the NAT, not the infected machine. Unfortunately, we can only see what’s coming from the NAT (public) IP; anything inside your network is visible only to you. You can start logging at the router or firewall to see what’s trying to use port 25 and that should lead you right to the compromised device(s).
In order to explain a sinkhole, first we need a brief explanation about how botnets work:
- Most botnets are controlled through the use of Command and Control (C2) servers.
- C2 servers are set up to accept connections from members of the botnet (the infected computers) and give instructions on what the botnet is to do.
Many of the simpler botnets use a limited number of static (unmoving) C2 servers that are reached by IP address or domain name, and rely on staying hidden or located in places who are willing to ignore criminal behavior for long term survival.
More sophisticated botnets use what are known as an “domain generation algorithm” (or DGA) to periodically generate a new set of domain names. The DGA uses a “pseudo random” algorithm that permits the botnet controller to predict what the domains are at any given time in the future.
- The botnet controller merely has to register one (or a few) of these domain names and point them at C2 server(s) to issue commands to the botnet.
Sinkholes
Anti-botnet researchers and law enforcement can often identify existing C2 domains or predict DGA domains in the same way that botnet controllers do.
They can often acquire the domain and point it at a server of their own. These are called “sinkhole servers”, or simply “sinkholes”.
- Generally speaking sinkholes provide no instructions back to the infected computers, and merely record who connected to them.
Sinkhole servers are used for the following reasons:
- They can prevent the infected computers talking to the real C2 servers and thus prevent them
from doing damage.
- To perform basic research on the botnet – eg: how many infected computers there are.
- To provide lists of infected machines for notification/remediation/repair.
If your IP is hitting a sinkhole, blocking the IP from connecting to the sinkhole is not going to fix the botnet infection. Please find the infected machine and fix it. If needed, call professional assitance.
What is TOR? Why does it exist?
The Onion Router (TOR) is free and open-source software designed to enable anonymous communication. It directs and routes Internet traffic via a free, worldwide, volunteer overlay network. It is intended be used by political dissidents, “whistleblowers” and users who have a strong desire for privacy.
From the destination service’s perspective, the IP address making the final connection to them is called the “TOR exit node”.
More information can be found on TOR at the TOR Project
What is a VPN?
A Virtual Private Network (VPN) is a mechanism for creating a secure connection (tunnel) between a computing device and a computer network (or between two networks) using an insecure communication medium such as the public Internet.
- Unlike TOR, VPNs are usually a commercial service.
- VPNs generally apply to all traffic the user wishes to send, including email, web traffic, streaming, etc.
- There are many VPN providers, who offer (usually commercially) these services to customers. Each VPN tunnel may forward just one user’s traffic or many.
- Not all commercial VPNs are created equal. Some may spy on your traffic, some may use your bandwidth without your knowledge. If you choose to use a VPN, choose wisely.
Why does the XBL sometimes list TOR/VPN/etc IPs?
Not only do political dissidents and people with elevated privacy concerns want the anonymity provided by using TOR or a VPN, common criminals do as well for obvious reasons. TOR exit nodes and VPNs are heavily used and abused by criminals worldwide to facilitate spam, financial and data theft, identity theft, DDOS, phishing and compromising innocent third parties via malware, botnets, spambots and other similar activity.
Introduction
People often find that they have a XBL listing that corresponds to the network address translation (NAT) IP for a local area network (LAN), and that identifying the infected machine can be extremely difficult.
This FAQ goes over a number of methods for identifying infected machines on a LAN. Many of these methods require specific technical knowledge to implement.
The first thing to do is to secure the firewall to limit access to outbound on port 25, allowing only SMTP server(s) on the local network. Remote sending of email to servers on the Internet should still work if web-based, or configured properly to use port 587 using SMTP-AUTH.
Once that is done, that still leaves the problem of finding the infected device. Unfortunately, we can only see traffic coming from the NAT IP; anything inside the network is visible only to someone with admin access. We hope the following information will help.
Why is my AV/AM scan not finding anything?
These days many bot infections cannot be found by anti-virus or anti-malware “cleaners”. This means you can spend a large amount of time and effort running your A/V tools on every device on your LAN and find absolutely nothing – or find something that is not related to the XBL listing.
As a result of this, even if it is known which device is infected, usually the A/V tools can not fix them; the software will have to reinstalled.
What am I looking for?
You are attempting to find out which device is making unwanted connections on port 25. When dealing with a large network (such as an office building) you will want to use some kind of network sniffer or firewall logging tool. Many of these tools require significant network administration expertise: if necessary, a consultant or other professional that understand these tools should be hired. The simplest methods in the “Centralized Detection”section use a network sniffer or firewall logging.
- If your LAN uses an ethernet hub (not a network switch or router), or your firewall is a generalized computer (eg: Linux or Windows server acting as a firewall) go directly to the port 25 sniffing section below.
- If you’re not using a hub, sniffing is still possible, but it’s harder, and using one of the per-machine methods may be simpler. If you have a decent firewall that has logging capabilities, go to the section on Firewall logging.
What am I NOT looking for?
XBL catches things that do not go through normal mail servers. These spambots have their own proxy or SMTP client built in, and they connect directly to the internet on port 25, bypassing any legitimate SMTP server.
- SMTP server logs will show nothing.
- Telnetting to the mail server on port 25 will not work to determine the HELO value. Telnet to port 25 on the mail server shows the “banner”, not the HELO.
- HELO settings can be tested by sending an email from the listed IP to “helocheck@abuseat.org”. A bounce that contains the required information will be returned immediately. It will look like an error, it is not. Please examine the contents of this email. (Note: this does not work with IPv6 at this time)
- If the HELO value is expected and correct, there is another problem, usually malware or a spambot.
Methods to try on individual devices
The methods in this section require that each device in the LAN be checked one at a time.
- If there are a number of devices to check, downloading some of the tools we mention and putting them on a USB key can help.
**NOTE:**We recommend trying the tools mentioned here before spending a lot of time on A/V scanners.
tcpview/tcpvcon (Windows OS) [EASY TO USE]
The tools “tcpview” and “tcpvcon” are free and can be downloaded from Microsoft
- Navigate to where you’ve placed “tcpview”, and run it. It will display all of the programs that have network connections open – naming the program, protocol, local address and port, remote address and port and state.
- You’re looking for lines that show these in the remote address: “:smtp” or “:25”. This indicates a remote email connection.
- A correctly set up device that uses SMTP-AUTH on port 587 or 465 should not show any of these.
- When a connection is freshly established, the corresponding line is green and when the connection ends, it is shown in red briefly before disappearing.
- If you have found the device with a spambot, the display will show numbers of green “:smtp” lines appearing and red **“:smtp”**lines disappearing. Watch the display for a few minutes to see if any “:smtp” lines show up and disappear. If they do, then that device has a spambot!
CAUTION! If you find a device with the bot showing up on tcpview, do NOT simply delete the corresponding program. It is probable that it is an infection inside a legitimate Windows program! Simply deleting it could cripple the computer.
Get and run as many anti-virus programs as possible, and see if any of them detect or remove the infection.
- If any of the scans say they have found something, follow the instructions to remove it and reboot the machine.
- Run “tcpview” again, and watch it for a while.
- If the problem recurs, you will probably have to reinstall the computer from scratch
Note: There are some bots that have their own TCP stacks. “tcpview” will probably not see activity from these.
Netstat (*NIX and Windows) [EASY-MEDIUM to use]
Netstat is standard on most versions of *NIX. Most versions of Windows also have it. The main difference is that netstat is a command line function that takes a single snapshot of current connections. In many versions of netstat, the most effective command line to use is:
netstat -napThis can show an active infection like this:
Active Internet connections (servers and established) Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name tcp 0 1 192.168.2.2:58246 212.69.102.240:25 SYN_SENT 12614/b.pl tcp 0 0 192.168.2.2:35843 209.85.201.27:25 ESTABLISHED 7996/ciwhcnsb.pl tcp 0 0 192.168.2.2:53051 81.13.48.2:25 TIME_WAIT - tcp 0 0 192.168.2.2:53623 77.243.121.126:25 TIME_WAIT - tcp 0 0 192.168.2.2:57816 217.13.210.81:25 TIME_WAIT - tcp 0 1 192.168.2.2:50531 217.16.16.81:25 SYN_SENT 12270/nxhbo.pl tcp 0 0 192.168.2.2:52437 217.198.11.26:25 TIME_WAIT - tcp 0 1 192.168.2.2:50140 195.64.222.2:25 SYN_SENT 9273/yzezihd.pl- The “:25” at the end of “Foreign Address” indicates an outbound SMTP (port 25) connection.
- “NNNN/name” under “PID/Program name” is the process id and process name of the program.
- The large variety of “states” show that it is starting up/shutting down connections very quickly.
On Windows, use this in a DOS command window:
netstat 5This will give you a list of all network connections your machine has open, that will refresh every 5 seconds until it is stopped. This will look very similar to the “netstat” output above.
- Microsoft and other familiar names will show up – they’re normal (from your browser, social media etc). “Akamai” is normal too.
- There will usually be a lot more lines than the above that do not have “:25”, those are other non-email connections. You might want to repeatedly pipe the output of “netstat -nap” through “grep :25” to only see the SMTP connections.
- “:25” on the local address means an inbound connection.
- “Many outbound port 25 connections” is the usual sign of infection.
NOTE: Depending on the infection, you often won’t be able to find the programs, because they start up, delete themselves from the file system, and continue running in memory.