news
Want to submit data? Be our guest!
In this News Article
Jump to
For many years Spamhaus has been asked if it accepts data from third parties. The standard response has always been “Only after a detailed technical process and if certain criteria is met". But today, that response changes to “Yes, we do”. If you want to submit malicious domains, IPs, email source code or URLs there is now a portal available for non-security professionals and threat hunters alike, at https://submit.spamhaus.org, called the Threat Intel Community.
Why now?
Community is at the very heart of the Spamhaus Project. Many, many moons ago, our founder, Steve Linford, sat aboard his houseboat on the river Thames, growing increasingly irate about the number of spam emails he was receiving. He took it upon himself to list the IPs associated with this spam avalanche, and shared the data so internet users could block connections to these IPs. Before long, like-minded individuals joined Steve’s crusade. A community was born. One that was filled with passion and a desire to do what was right for the good of the internet.
Fast forward 25 years, and Google isn’t the only one celebrating its quarter of a century – so is Spamhaus. Here we are in 2023, and while the focus has shifted from pure spam to that of malware, phishing and ransomware, and from DNS Blocklists, to a wide range of threat intelligence, the importance of sharing data and signal remains at the core of what we do. So, what better year to launch the Threat Intel Community? It feels only fitting to provide the community with a place to share signal that is believed to be malicious, just as Steve shared those IPs back in 1998.
Who is the Threat Intel Community for?
Anyone. Honestly, anyone can make a submission. From your Dad, who has received a phishing email, whose knowledge of technology is limited, to an amateur threat hunter, who wants to submit thousands of potentially malicious domains via an API– there’s something for everyone.
What data are we accepting?
In its first iteration the portal will accept the following:
- IP addresses e.g. 8.8.8.8
- Domains e.g. example.com
- URLs e.g https://www.example.com/test
- Email source code e.g.
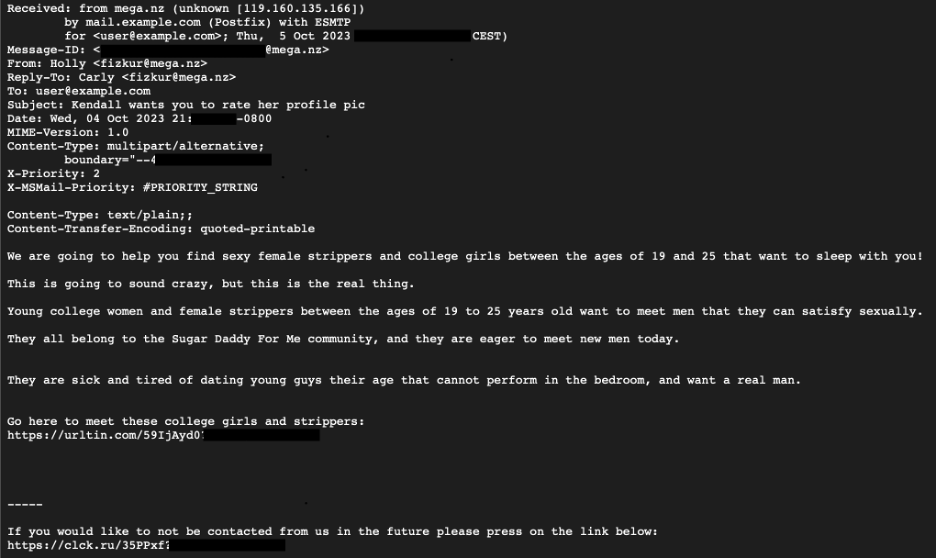
How do you submit the data?
There are three ways submissions can be made:
- A single guest submission. Complete a simple form, include your email, what type of threat you think it is, the reason why, and submit. You’ll be sent an email from Spamhaus to verify your email address after which point the form data will be sent through to Spamhaus.
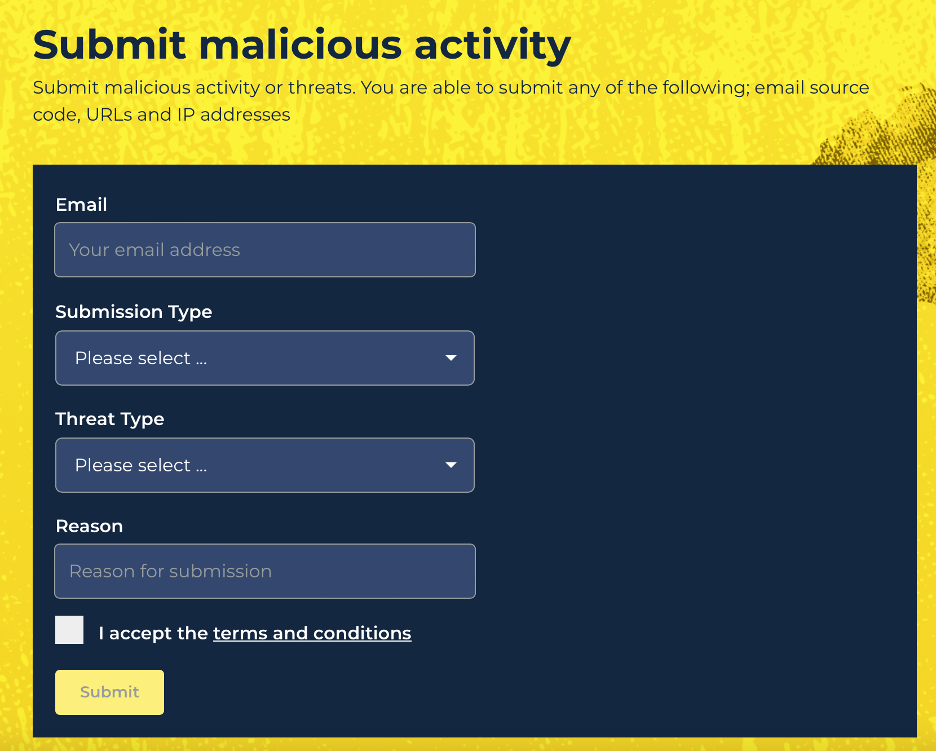
- A single account submission. Create an account via one of three authentication methods (Github, LinkedIn or Google), complete the submission form, including the type of threat you think it is, the reason why and submit... and then submit another and another... you get the picture!
- API submissions. For multiple submissions there is an API which needs to be used in conjunction with a key, which you can create through the account page once you’ve authenticated. To use this API, you do need to have some basic coding skills, however once set up you can submit as much signal as you like... actually that’s not quite true. It won’t come as a surprise to learn that we do have some rate limiting applied!
What feedback do you get?
For those of you who choose to create an account you will have a dashboard to show the number of submissions you have made along with the number of detections matched on Spamhaus’ datasets.
What’s next?
You tell us! What features do you want to see in this portal? We have a roadmap, but we want you to help shape it. Because this is built for you, the community.
Do you want somewhere to discuss threat hunting techniques and interact with Spamhaus’ threat hunters, for example a secure and managed Slack channel? What other type of data and threats would you like to submit? What feedback via the portal would you like to see. What free data would help you with your threat-hunting, for example, Passive DNS data? We welcome your feedback. Obviously, features won’t appear overnight, but we’ll certainly add them to the list!
Last but not least
A huge thank you to the Spamhaus team who have made this possible, from the Backend and Frontend Developers, to our OSINT team and Marketing who have all helped from ideation to production. And finally, “thank you to you”, our community, who have supported us for the past 25 years. Visit the Threat Intel Community website to learn more.
