blog
Sex education in the classroom? Google can help, but there is a compromise!
It’s not uncommon for popular services to eventually fall victim to abuse. In this case, we explore how spammers are using Google Classroom to lure their victims (at elementary school!) to dating websites and generate revenue via affiliate programs associated with such sites.
In this Blog
Jump to
What is Google Classroom?
Google Classroom is a web-based learning management system introduced in 2014 that has attracted users from all over the world. It provides teachers with a free platform to run and manage classes online. The concept of classroom education has been around since the ancient Egyptians and has always played a fundamental role in the education system. However, with the outbreak of the global COVID-19 pandemic in March 2020, utilization of online services like Google Classroom has skyrocketed. As with other online services, this also introduces new security challenges. Many schools that use the Google Classroom service are falling victim to online abuse, with many accounts found to be compromised, used for spamming, and other malicious activity - including the ‘Secret Sex Club.’
The Compromised Classroom
You might be fooled into thinking this ‘club’ is a new extracurricular class. What teacher wants to deliver sex education face-to-face in a classroom of awkward teens? If only it were that innocent. Sadly, this club has a more sinister objective. And it all starts with a mysterious Google Classroom message sent to a Google Mail address requesting you to join a Secret Sex Club.
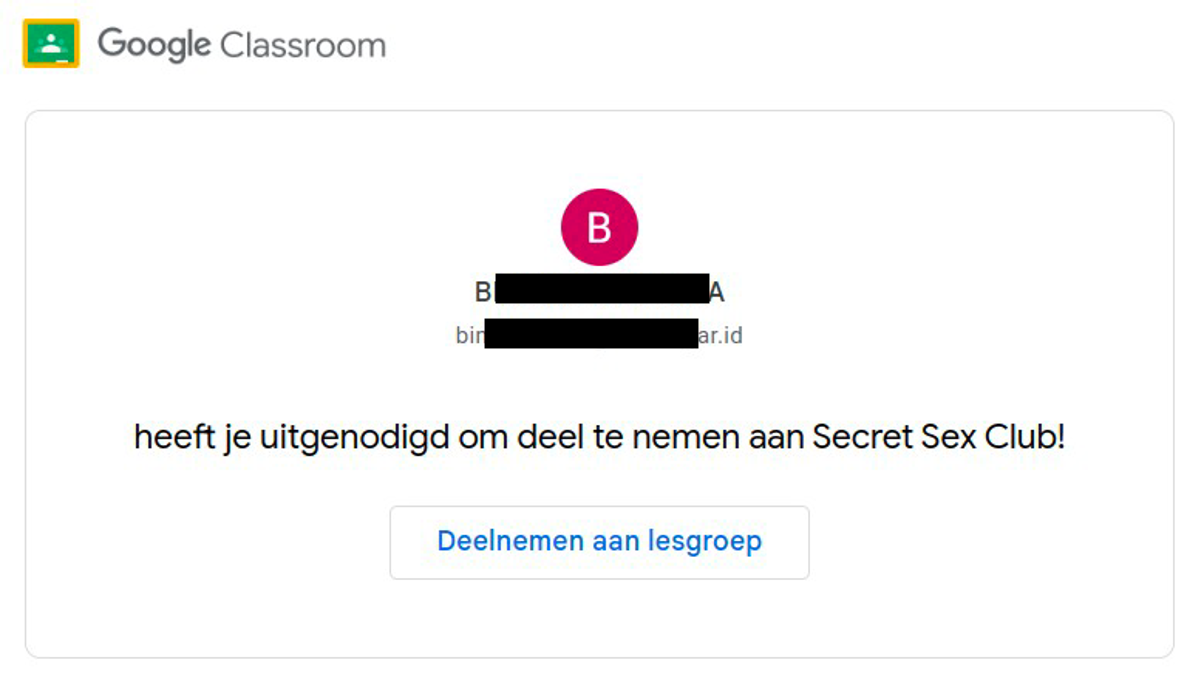
Once accepted to join the “class” using your gmail.com address, you enter the classroom and are presented with a message, including a link set up by the adversary.
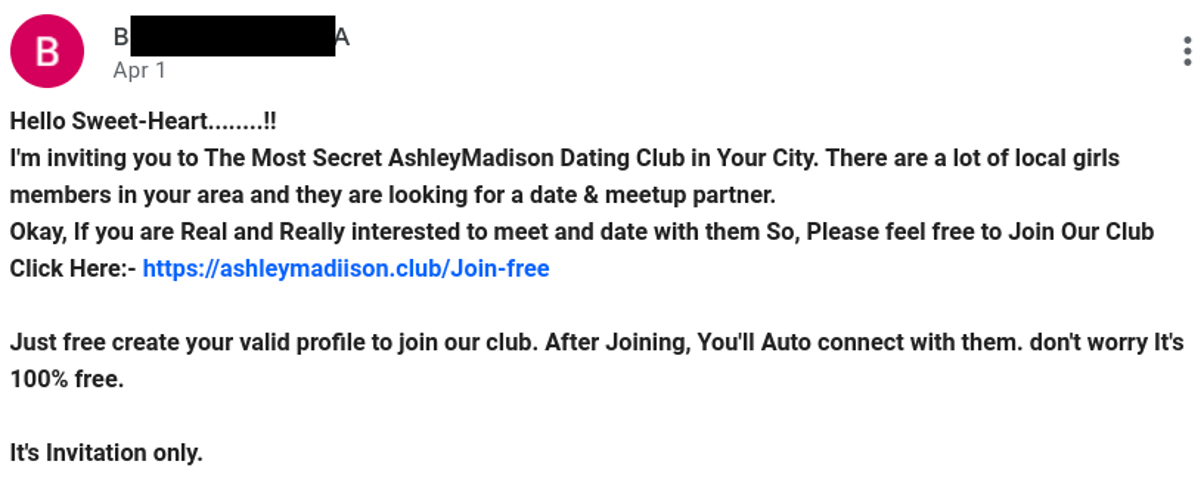
It might not be apparent to the untrained eye that there are two immediate signs that the domain in this message is untrustworthy. The first sign is the "ii" typo in "ashleymadiison" a common tactic used by miscreants. The other less obvious sign is the “.club” top level domain (TLD). This is a low-reputation TLD commonly used by spammers for short-term usage.
However, this throwaway domain closely resembles the legitimate Ashley Madison dating site - a Canadian online dating and social networking service. And it’s this domain that serves as a starting point for the landing page of a dating service associated with your geographical location.
Discreet in nature
Spamhaus researchers used an IP address based in the USA, for the investigation. Upon clicking the link, you are directed to what appears to be a fake Ashley Madison website: ashleyrnadison.com. Did you spot the “rn” typo that deviously reads as an “m”?
According to this blog post, however, it appears to be the real deal:
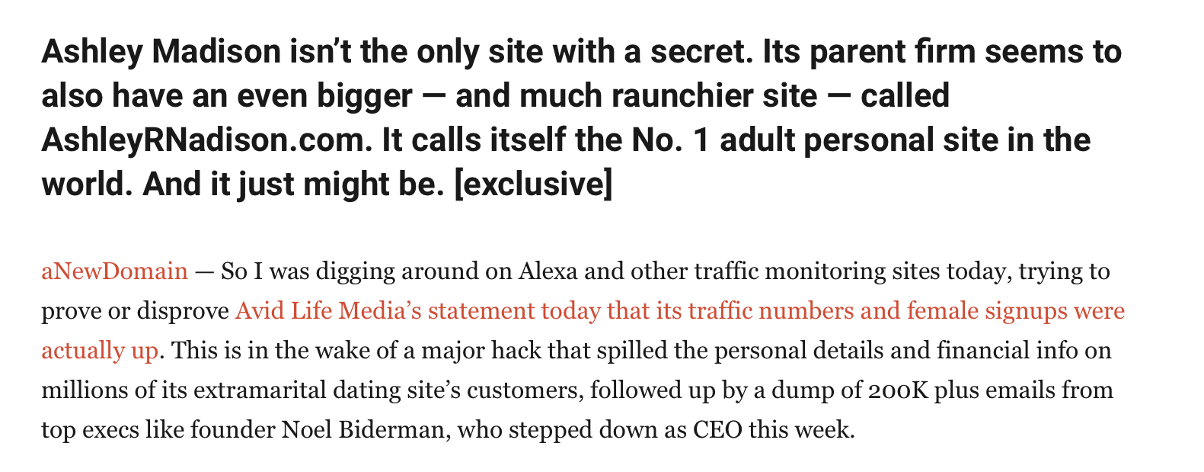
https://anewdomain.net/ashley-madison-bigger-sister-adult-personals-site-ashleyrnadison-from-avid-dating-services-exclusive/
As only the most motivated individuals will spend time analyzing the spam message and analyzing websites the traffic is being driven to, the affiliate program manager at Ashley Madison is unlikely to discover this.
Should someone from Ashley Madison read this post, this is the information you need to identify the abusive user and take action:
offer_id=8&affiliate_id=1955&affiliate_sub=DLO-8197
How is this relevant to schools?
The vast majority of compromised accounts appear to be associated with schools in Southeast Asian countries, including Indonesia and Thailand. The spammers don’t appear to have a way to forge or obfuscate this information, so we can see a clear picture of which schools need to tighten their Google accounts:
jo****69 (at) anubancp.ac.th
ca****69 (at) anubancp.ac.th
bi****8 (at) sd.belajar.id
bi****33 (at) sd.belajar.id
Although “anubancp.ac.th” doesn’t appear to have a working website anymore, a quick search points to “โรงเรียนอนุบาลชุมพร", which translates to Anuban Chumphon School, an elementary school - ages 5-11 - based in Southern Thailand. “belajar.id” (Merdeka Mengajar) is an education platform aimed towards Indonesian schools and institutions.
How can schools protect their users?
Without a detailed understanding of how the Google Classroom interface works and the tools available to users, it’s difficult to offer technical guidance on how to protect users. General security best practices should always be followed, as described in Google's how to make your account more secure. Strong passwords, 2-step verification, reviewing third-party access to your data, updating all software, and disabling any inactive accounts are all recommended.
Unfortunately, until Google addresses this issue and takes action against abusive accounts on its platform, this problem will persist. Unlike in the classroom, no one will be getting detention anytime soon!