blog
Abuse takes its “toll” on .top: But who is paying the price?
Despite ICANN issuing a formal notice to .top citing a breach of contract for failing to address DNS abuse, the situation has not improved. Over the last six months, abuse of .top hasn’t just persisted, it’s gotten 50% worse! So, why is this happening, and what can be done to stop it?
In this Blog
- Let’s start with what we’re seeing
- So, what exactly do we know about .top?
- What makes .top and .xin such magnets for abuse?
- There’s always time to turn it around!
- Enforce Know-Your-Customer procedures:
- Clamp down on bulk registrations:
- Introduce financial barriers:
- It’s time to hold those responsible, accountable
Jump to
Let’s start with what we’re seeing
In the latest Domain Reputation Update, Spamhaus researchers observed a 50% increase in abuse of the generic top-level domain (gTLD), “.top” with 211,406 detections in just six months. Among these detections was a surge in toll road scams, a trend also flagged in APWG’s Phishing Activity report.
Two examples of this scam include domains targeting E-Zpass, an automated toll paying system on the US east coast, and FasTrak its west coast equivalent.
e-zpass.com-txzy[.]top
bayareafastrak.com-fzxb[.]top
Delivered primarily via SMS phishing - or “smishing” - these scams exploit the .top TLD to trick recipients into believing they owe unpaid toll fees.
Here’s how the scam works using:
- The first thing you receive is an SMS (text) message claiming you have unpaid tolls or an outstanding balance. The messages often warn of fines or even the loss of your driving license if you don’t pay immediately.
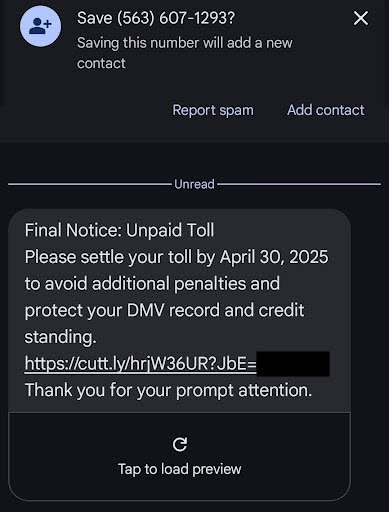
- Within the message is a phishing link that leads you to a fake website posing as a genuine toll payment portal.
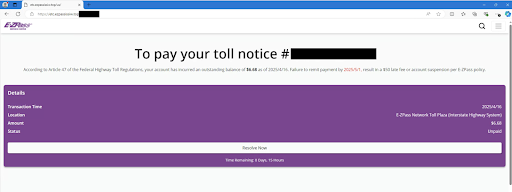
- The fake website asks you to enter your credit card number, bank account number, or other personal details.
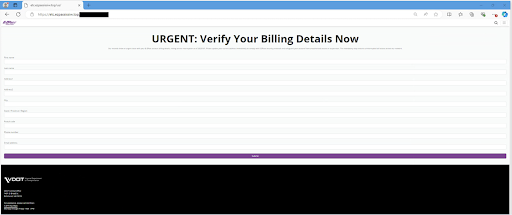
- Finally, the stolen details are used by the scammers for fraudulent activities.
The perceived legitimacy of the website, combined with the sense of urgency created through the messages, provide scammers with the perfect trap. And it’s the ongoing proliferation of such scams that underscore .top’s failure to properly oversee and prevent abuse.
After being live for several days, and stealing credentials, we can confirm the site used in this example was taken down on May 4th 2025.
So, what exactly do we know about .top?
Managed by Jiangsu Bangning Science & Technology Co., .top was first introduced in 2014 aimed at businesses looking to highlight premium or "top" services. By 2017, this TLD had become China's most registered domain name even overtaking .com and .cn domains. However, its low-cost registrations and minimal oversight have made it a hotspot for abuse.
And it’s not alone. Another TLD, .xin, operated by ElegantLeader Limited, has also been linked to fraudulent activities. Appearing in the latest Domain Reputation report, .xin has also been tied to toll road scams, and abuse utilizing hyphenated domains like 'com-tollbillx.xin' that exploit the credibility of TLDs like .com.
Even more concerning? Both .top and .xin domains are primarily registered through Dominet (HK) Limited, a registrar that until August 27, 2024 operated under the name “Alibaba.com Singapore E-Commerce Private Limited”. Why the sudden name change, you might ask? It came exactly five months after ICANN issued a compliance notice on March 27th, 2024, citing the registrar’s “failure to take reasonable and prompt steps to investigate and respond appropriately to reports of abuse” - the very same issue raised with .top.
Coincidence? Given .top’s track record, it seems unlikely.
What makes .top and .xin such magnets for abuse?
Unfortunately, both .top and .xin tick nearly every box of “how not to manage abuse”, including:
- Low cost registrations
- Minimal registration requirements
- Wide availability
- Bulk registration support
On top of that, relationships with “abuse-friendly” resellers that fail to perform meaningful vetting, only worsen the situation. With some even turning a blind eye to favour profits!
There’s always time to turn it around!
Even small changes can lead to significant improvements. So, what practical steps can registries and registrars facing ongoing malicious activity in their TLDs take to restore trust and protect users?
Enforce Know-Your-Customer procedures:
To avoid a TLD with hundreds of thousands of problem domains like .top, registrars need to improve customer vetting at the point of registration. This could include: verifying contact data, querying business registries, and only adding domains to DNS once verification is complete.
Clamp down on bulk registrations:
Do not allow new and/or unverified users to make bulk registrations. To verify users, request additional identity checks and prevent fraudulent registrations. Automated registrations with junk names and registration information should not be processed, such as:
Domain: com-tollbillalu.xin
Registrant Organization: asdad
Registrant State/Province: asdasd
Introduce financial barriers:
There’s no escaping, the vast majority of newly registered malicious domains exist at the lower-priced tiers - a trend seen consistently in Spamhaus’ Domain Reputation Reports. Many TLDs have low prices for registration and higher prices for renewal. Unsurprisingly, this incentivizes cybercriminals to quickly replace suspended domains.
A better strategy? Increase the financial barrier. Instead of a blanket approach, sellers might consider tiered pricing models where high-risk domains or frequently abused patterns cost more to register.
Unfortunately, .top’s actions - or lack of - suggest little intent to "do the right thing." As the issue appears to be much deeper, external intervention appears to be the only viable solution.
It’s time to hold those responsible, accountable
Yes, policymakers, we're talking to you.
Issuing breach notices is a start, but it’s clearly not enough. So, what’s really needed? Stronger, enforceable compliance measures for registries with persistently high abuse rates and a review of the effectiveness of actions taken. When it comes to .top, what meaningful consequences are on the table for repeated violations? Are financial penalties being considered - or even contract termination for ongoing non-compliance?
Right now, .top isn’t just skirting the rules, it’s blatantly disregarding them. And the spotlight isn’t only on .top, but on those with the authority to stop the ongoing abuse. Yes, ICANN has taken a first important step by issuing a formal notice, but it hasn’t moved the needle.
We urge ICANN to take a closer look and intensify its efforts to tackle this escalating abuse. It's time to hold .top and its enablers accountable for their role in enabling abuse. Spamhaus would welcome being part of this conversation to provide more data, insights, and recommendations to help drive meaningful change.