blog
The holiday hack – a reminder of why you shouldn’t always trust emails
Here’s a cautionary tale to anyone and everyone who uses email. The learning is simple: Always be vigilant, especially if its content asks you to provide personal information or click on links and download files.
In this Blog
Jump to
Introduction
Here’s a cautionary tale to anyone and everyone who uses email. The learning is simple: Always be vigilant, especially if the contents of an email ask to provide personal information or click on links and download files.
It started with a database breach
As the pandemic is becoming endemic, many countries have created dedicated registration programs to facilitate tourism. One example is Thailand’s Thailand Pass. Travelers must upload Covid test results and their vaccination status to help border security manage entry into Thailand.
Unfortunately, this database of travelers got hacked recently, as detailed here. Many tourists got caught in the malspam campaign that kicked off after the breach. The Spamhaus researchers had the chance to analyze an infected machine of one such victim. Here is what they found:
Seemingly legitimate emails
Let’s call our unlucky tourist Mr X (original, we know!). Mr X’s flight was due to leave for Bangkok on the 22-Feb-22. Being an organized sort, he had already completed the required steps to get his Thailand Pass and was ready for his trip. But on 17-Feb-22, he received the following two emails:
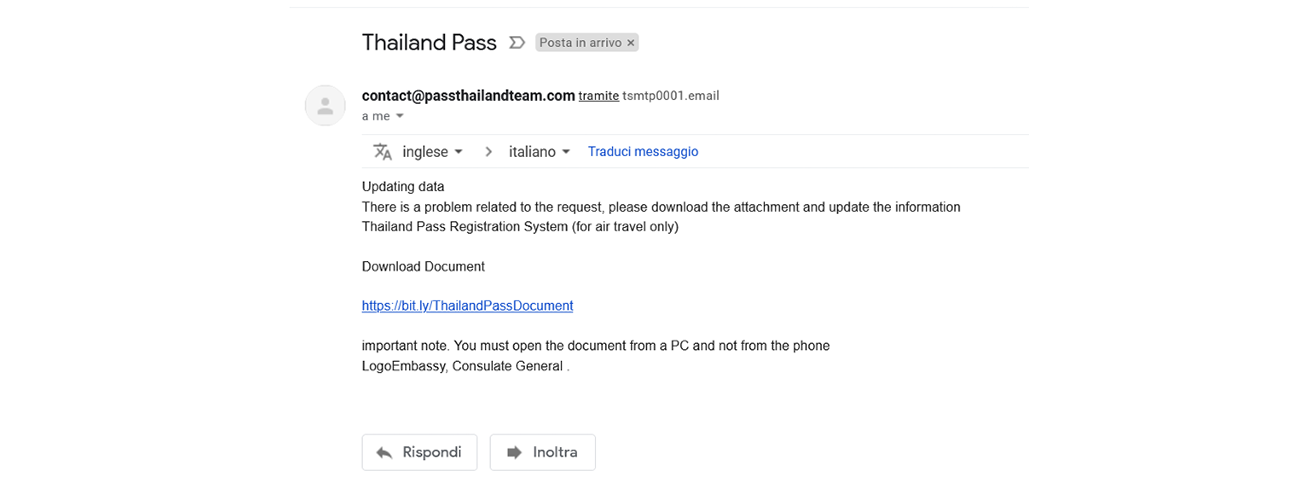
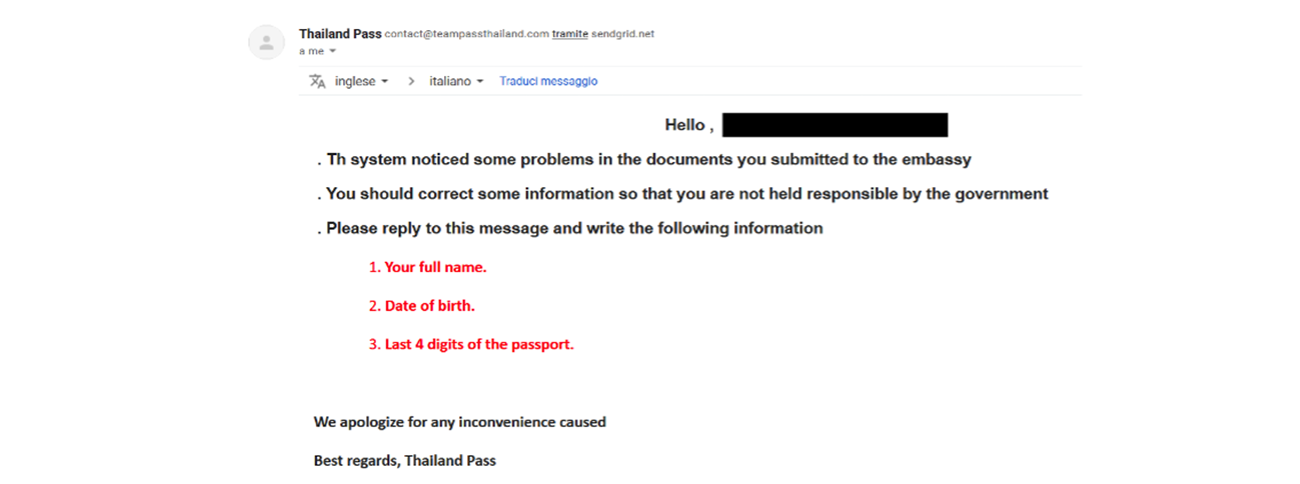
You will note that the sender domains are passthailandteam.com and teampassthailand.com. These domains are definitely not related to the Thai government. However, if you don’t spend 24/7 looking for malicious emails, it’s understandable that they could easily be deemed legitimate.
With a little research, one can establish that these domains were registered on 15-Feb-22 and 16-Feb-22, respectively, just days before the miscreants used them to send email. In our world, this usually raises a giant red flag – how often do you register a domain and immediately use it? The answer is almost never!
Back to Mr X, who was due to fly five days after receiving the above two communications – these emails panicked him. Who wouldn’t be unnerved? Here he was busy picturing himself landing in Bangkok, making his way to the beach and drinking a Singha beer, watching the world go by, only to suddenly think he may not be allowed even to enter the country.
Diligently Mr X followed the instructions in the email, providing his full name, date of birth, and the last four digits of his passport number. The reason for requesting these details? We can’t be sure, but we strongly suspect it’s related to identity theft.
Meanwhile, the link in the second email led to a website where a ZIP called “qr_thailand_pass.zip” was downloaded. Once opened, the ZIP contained a seemingly innocuous HTML file that, when opened, showed the following webpage:
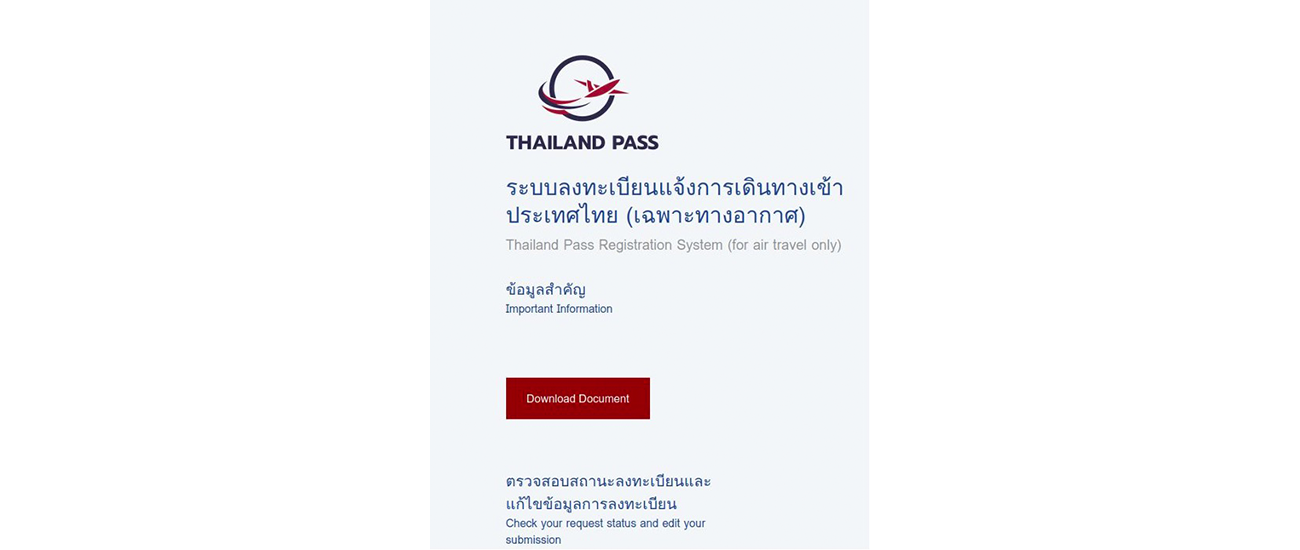
Once Mr X clicked “Download Document”, a VBS file called “status_report.vbs” was downloaded. In reality, the file wasn’t “downloaded”; instead, the HTML page contained some javascript code that mimicked a download. When double-clicked, the VBS file shows the following rather innocuous popup:
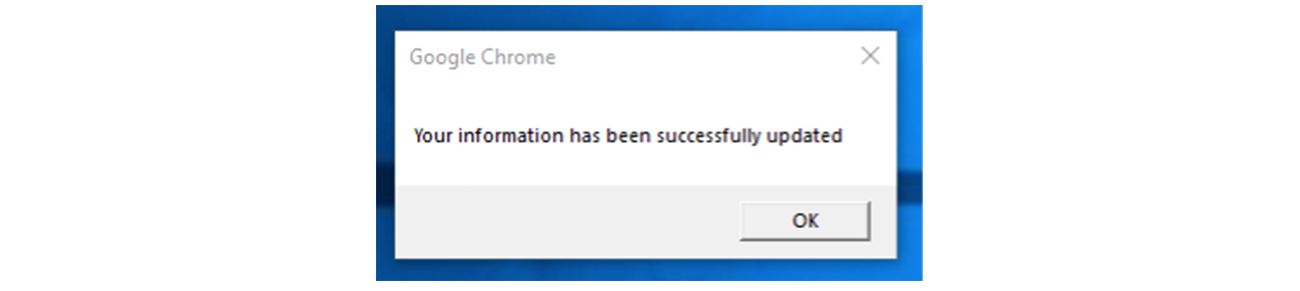
However, in the background, the VBS file downloaded and executed a Remote Administration Tool (or RAT) from https://archive.org/download/auto_20220216/auto.txt.
What’s interesting to note is that the miscreants hosted their malicious payload on “archive.org”. This is a very well-known website with a good reputation. In doing this, the cybercriminals were most likely trying to evade security software blocking websites with poor reputation.
What’s that credit card charge for?
Without giving these emails another thought, Mr X happily went on his trip. While in Thailand, on 02-Mar-22, he received a notification from Google Cloud Platform (GCP) with a charge of €93. Since he had some services with Google, he dismissed the notification as one of the usual recurring charges and continued to enjoy his vacation.
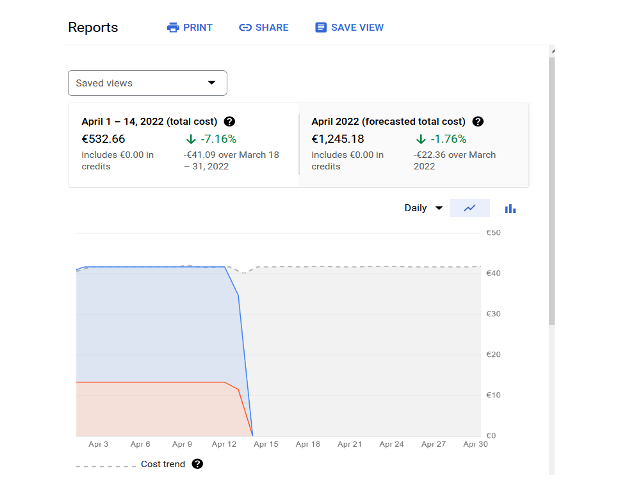
March passed, and Mr X received a notification from GCP that its charges for the past month were almost €1600! Suddenly alarm bells were ringing, so he contacted the Spamhaus researchers to investigate further.
The team uncovered that the crooks had created an exceptionally “CPU-hungry” Google Compute Engine (GCE) instance that had been grinding away for the whole of March and into April until they shut it down.
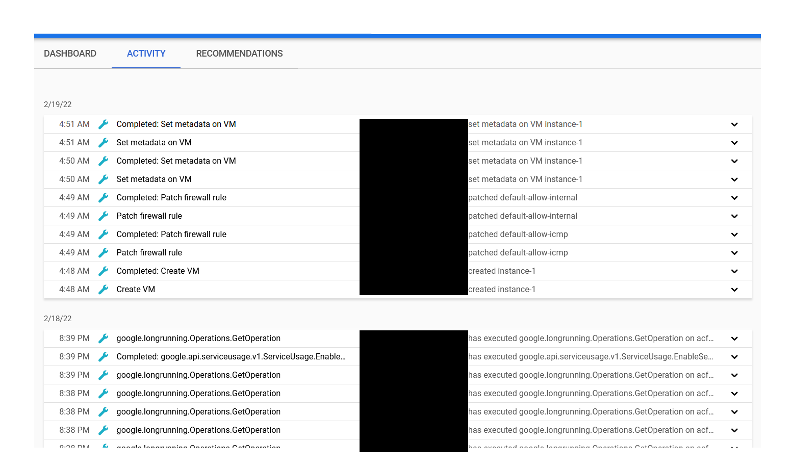
Upon reviewing the platform logs, they established that the instance was created on 18-Feb-22, only a few hours after Mr X downloaded and executed the infected file on his computer.
Before deleting the GCE instance, the Spamhaus researchers accessed it and found a Monero coin miner running, in addition to a RAT. This explained the huge charges – GCE bills are based on CPU usage, and mining cryptocurrency is a highly intensive process when it comes to CPUs.
“Whoah, surely Mr X has multi-factor authentication (MFA) on his Google account?” you may be asking. “How did the miscreants manage to create the GCE instance?” The answer is that both activities logged on 18/Feb/22 and 19/Feb/22 coincided with Mr X having his computer powered on. The hackers used the previously installed RAT to take control of Mr X’s machine, and since his browser was already logged in to his Google account, they didn’t need MFA to create the GCE instance.
What was the outcome for Mr X of this holiday hack?
Fortunately for Mr X, the credit card company reimbursed the fraudulent expenses. However, he also had to have his compromised passport cancelled and a new one reissued… Mr X is an Italian resident. To anyone who has had the misfortune to deal with Italian bureaucracy, you will sympathize with Mr X, understanding what an arduous and painful process this was!
What can you learn from Mr X’s misadventure?
- Always check emails
- When an official-looking email reaches your inbox, look for spelling mistakes. Reputable organizations don’t make them!
- Carefully review the sender domain. If it’s not the one you have had interactions with previously, be suspicious.
- Do not ever, EVER, run VBS scripts
- Beware of URL/link shorteners, e.g. “bitly”. They are often used to hide malicious websites.
- Always check billing notifications carefully – even if you are busy or on holiday.
- If you are compromised keep detailed records – When issuing a formal complaint to a credit card company, be sure to have a clear timeline of the events and provide as much information as possible.
Keep safe (not only on your travels) – it doesn’t take huge technical knowledge to follow the above points, and it could save you a significant amount of time, money, and stress that goes with falling victim to malicious internet behavior.