how-to
DNS Blocklist Basics
DNS blocklists should be your first line of defense against spam and other email-borne theats. Here is an intro to some DNSBL fundamentals.
In this How To
Jump to
Introduction
You’re running your own email infrastructure, or at least considering it, but how should email filtering be handled? What is your first line of defense against the spam and malicious emails that will bombard your mail server?The answer is simple – Domain Name System Blocklists (DNSBLs). However, if you’re not familiar with DNSBLs, it’s not going to seem simple, or at least, not initially. Don’t worry. We’re going to revisit some blocklist fundamentals to bring you up to speed.
DNSBL, blackhole list, blocklist, or blacklist?
Firstly, let’s try and eliminate any confusion around terminology. Are they called “blacklists,” “blackhole lists,” “domain name system blocklists,” or “real-time blocklists”?
The answer is….all of the above (and probably more). However, for this article’s purpose, we’ll be referring to them as “DNSBLs” and the simplified version of “blocklist.”
What is a blocklist?
The name gives it away; it’s a list, or more accurately, a database containing IP addresses, domains, or hashes. These lists are compiled by specialist research teams, who have observed the listed internet resources to either be:
- Directly involved in malicious behavior, e.g., sending spam, distributing malware, hosting botnets, hosting phishing websites, etc., or
- Having a bad reputation associated with them.
Presented in a DNS zone, blocklists can be utilized by anyone managing their own email infrastructure. Fundamentally there are three stages where you should be using DNSBLs:
- The initial set-up of a connection against the connecting IP address
- The ‘pre-data phase,’ i.e., during the Simple Mail Transfer Protocol (SMTP) connect
- The ‘post-data phase,’ i.e., the content filtering stage.
How are blocklists compiled?
It all starts with data. Vast quantities of data. In fact, Spamhaus was dealing with ‘big data’ before ‘big-data’ became the buzzword we know it as today.
The industry and beyond shares data with Spamhaus, from hosting companies to Internet Service Providers (ISPs) and internet governing bodies. Of course, in addition to this Spamhaus runs its own spam traps and honeypots.
Through manual investigations, machine learning, and heuristics, our researchers analyze this data to see if it meets pre-defined policies for listing.
How are the policies defined?
Before curating a DNSBL, Spamhaus decides on the criteria the IP, domain, or email content must meet for it to be listed. These criteria are referred to as “policies.”
Needless to say, these policies aren’t plucked out of thin air. Instead, they are formed in consultation with the wider internet industry (both senders and receivers) to ensure they are fit for purpose and meet internet users’ needs.
How much data is processed to produce blocklists?
To understand the breadth of data processed by our research team to produce reliable and effective blocklists, here are some daily numbers:
- 3 million domains assessed
- 18,000 malware samples processed
- 9 billion SMTP connections analyzed
- 100’s of heuristics used to identify the good from the bad
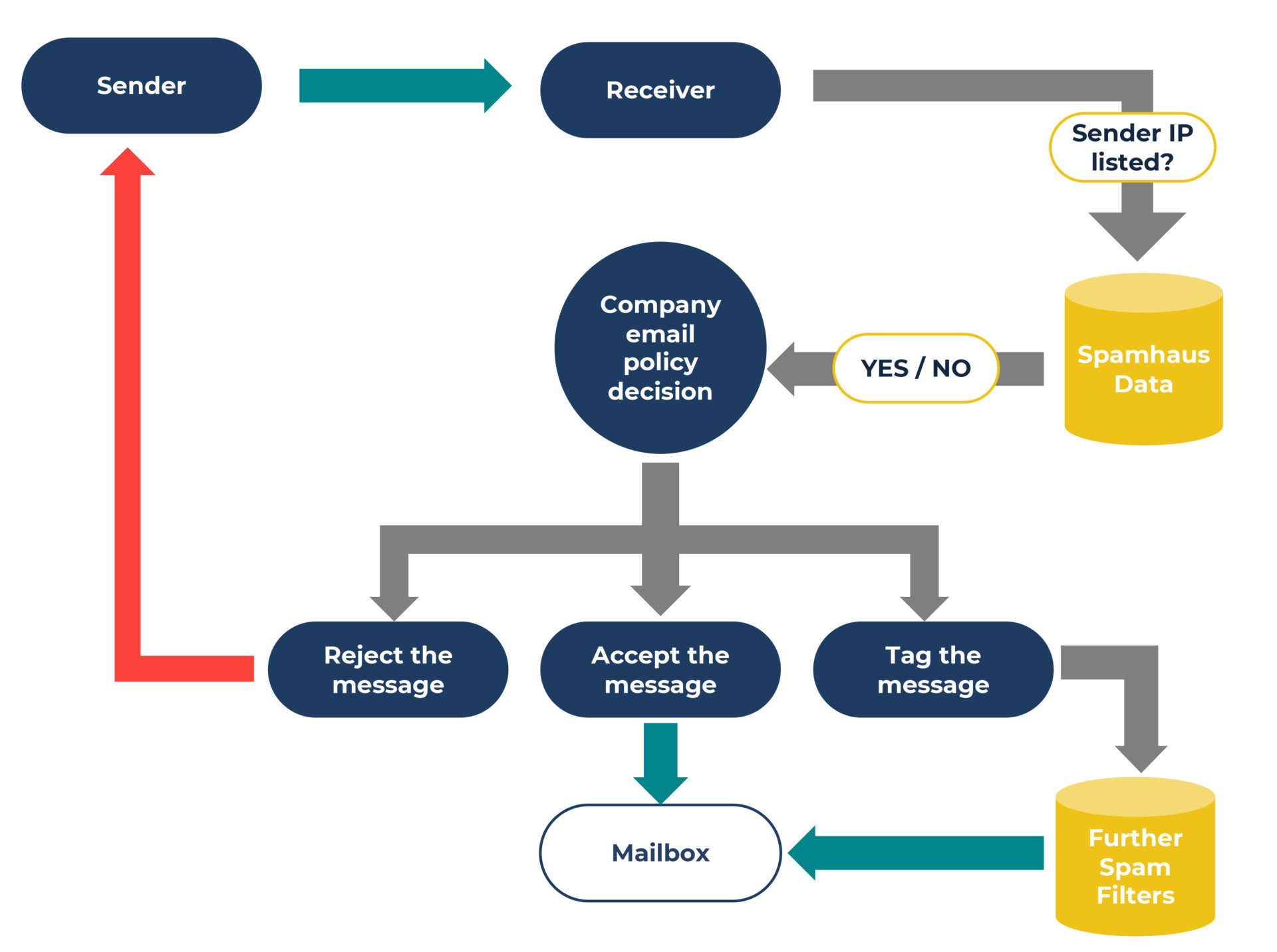
How blocklists work
The IPs, domains, or hashes associated with an email can be queried against a DNSBL to see if they’re listed. As someone managing the email infrastructure, it’s down to you to decide how to handle that potentially malicious email. You can either:
A. Reject the email in real-time, with an appropriate delivery code, or
B. Accept the message and tag it for additional filtering.
Read Understanding the source code of a malicious email to understand why certain parts of an email’s source code have specific blocklists applied to them.
What blocklists are available?
As previously mentioned, blocklists contain either IPs, domains, or hashes. Here’s a quick overview of the types of blocklists produced by Spamhaus:
Spamhaus Blocklist (SBL) – IP addresses observed to be involved in numerous activities including sending spam, snowshoe spamming, botnet command & controllers alongside hijacked IP space.
**eXploits Blocklist (XBL) –**Individual IPs (/32s) that are infected with malware, worms, and Trojans etc. This list prevents mail servers from accepting connections from compromised computing devices.
**Policy Blocklist (PBL) –**IP addresses that shouldn’t be sending email e.g. internet of things (IoT) devices. Spamhaus works together with the industry, enabling IP owners to list and manage their own ranges for your safety.
**Auth Blocklist (AuthBL) –**IP addresses know to host bots using brute force or stolen SMTP-AUTH credentials to send malicious emails.
Domain Blocklist (DBL) – Domains owned by spammers, being used for nefarious purposes. We also list domains that are legitimate but have been hacked by bad actors and are being used with malicious intent.
**Zero Reputation Domains (ZRD) –**Domains that have been registered in the past 24 hours – helping you filter email from cybercriminals who register, and immediately use multiple domains on a daily basis.
**Hash Blocklists (HBL) –**A content blocklist that uses cryptographic hashes to list email addresses, cryptowallet addresses, and malware files.
What’s next?
After this tour of some blocklist basics, why not try the data yourself. Sign up for a free trial here.