blog
Bad sushi: China-nexus phishers shift to residential proxies
In this Blog
Jump to
Introduction
Earlier this year, Spamhaus researchers noted a major shift in the phishing landscape targeting Japan: Commencing April, a China-nexus threat actor started leveraging residential proxy networks for disseminating their phishing emails, rather than sending them from a variety of subnets at China Telecom and China Unicom. In this blog, we look at the origins of the activity, drawing parallels to earlier campaigns, and discuss countermeasures to disrupt residential proxy-enabled spam operations.
Phishing spam emissions from China – an old phenomenon
Spam emissions from the networks of China Telecom and China Unicom networks are hardly a new nuisance, and have long been responsible for a considerable amount of listed IPs in Spamhaus’s datasets. Some branches of these internet service providers (ISPs) do better than others – it is crucial to track China Telecom and China Unicom on a branch/province-basis, as abuse handling and abuse prevention differs between these branches – but their networks never left Spamhaus’s top 10 of spam-emitting ISPs.
Looking closer, however, a peculiar pattern emerged: Some subnets disseminate spam in a way common dial-up pools do. Other networks show a much more consistent, systematic pattern of spam emissions, suggesting that they are not hosting boatloads of infected end-user devices, but are dedicated to spamming. Particularly at the Fujian branch of China Telecom, dial-up-style PTRs were (and are still) configured for these spam cannons, presumably to deceive postmasters and investigators. The vast majority of spam e-mails originating from these dedicated networks are phishing, targeting users in Japan.
Spamhaus encounters major, quasi-nation-state ISPs proliferating spam operations on a regular basis (a recent example is Tunisia’s Agence Tunisienne Internet), however, the spam emission situation at China Telecom and China Unicom notably sticks out by quantity – but not necessarily by quality.
If this isn’t new, what caused the change?
For years on end, both dial-up and dedicated spam networks of China Telecom and China Unicom have been listed in Spamhaus’s Policy Blocklist (PBL), a preventive dataset of IPs which, according to the dataset’s listing policy, “should not be attempting to directly deliver unauthenticated SMTP email to any Internet mail server.”
So, for users of Spamhaus’s datasets, these (phishing) spam emissions did not pose any threat, yet the threat actors continued disseminating them for years.
In February 2023, Spamhaus researchers started listing China Telecom and China Unicom subnets apparently dedicated to phishing emissions in the Spamhaus Blocklist (SBL), a different Spamhaus dataset covering – among other security threats – IP networks dedicated to spam emissions. Both PBL and SBL are bundled together in Spamhaus’s ZEN blocklist, so for its users, the additional SBL listings should hardly make any difference.
At least, that’s what we thought. However, having their spam cannons listed in SBL made the threat actors jump: On several occasions, phishing spam emissions from affected networks declined sharply, only to resurface at nearby subnets shortly afterwards. In some cases, networks seemingly abandoned by the threat actors appear to have been repurposed for genuine dial-up pool usage, according to our telemetry.
These observations suggest that many Japanese e-mail service providers were using SBL to protect their users, but not PBL or the combined ZEN dataset. Thus, it was only after SBL listings occurred that the threat actors saw their deliverability rates collapsing.
April 2025: The shift to residential proxies
This cat-and-mouse-game continued for a while. In the meantime, residential proxy networks had gained traction, fueled by a plethora of insecure or pre-compromised internet of things (IoT) devices, including smart doorbells; the threats emanating from such proxies to local networks and the internet long went unnoticed.
In early April, the China-nexus phishers joined the game, and started leveraging residential proxy networks for disseminating their phishing e-mails, at the tune of 3.5 to 4 million IPs, churning through ~250k IPs on a daily basis. Latin America in particular lit up in Spamhaus’s systems like a Christmas tree. (A few weeks prior to this development, a Brazil-nexus phishing campaign was observed abusing some 500k IPs tied to residential proxy activity for widespread brute-force login attempts.)
By May 2025, the source countries of this phishing campaign had gone from one (China) to 173, ballooning from around 4.6k distinct source IPs to more than 1.3m, involving a total of 8,893 Autonomous Systems (ASNs).
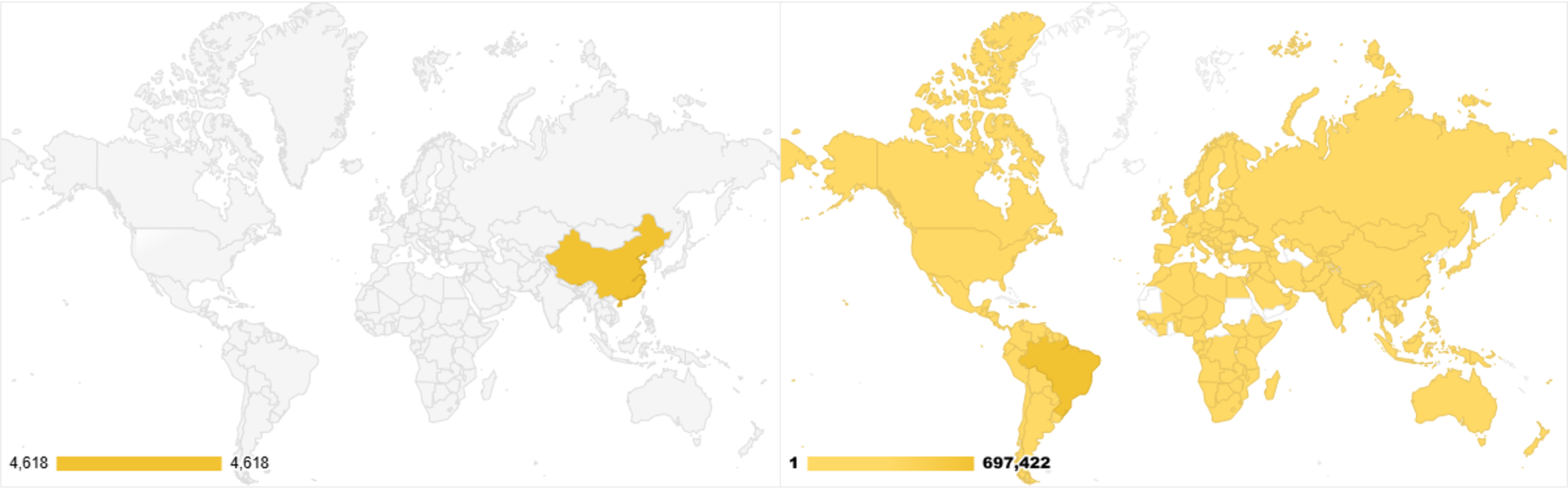
Previously, the campaign had been constrained to IPv4 emitters; the shift towards residential proxies entailed an explosion of IPv6 spam emissions, causing a surge in IPv6 listings in Spamhaus’s datasets as well.
Abusive activity proliferated by residential proxy networks has increasingly received attention since the early 2020s, however, it was not until this campaign’s shift that Spamhaus observed a scale and speed akin to the heydays of botnet spam in the 2000s.
The adoption of residential proxies also saw changes in spam e-mail characteristics: Instead of impersonating the targeted brand (popular choices of the threat actors are SBI, JCB, and Hodaka) during the SMTP transaction, phish spam delivered via residential proxies consistently used generic, non-existent HELOs.
So changed the phishing URLs, moving from shared file networks to the .top top-level domain (which has a considerable abuse track record), onto redirectors. Phishing landing pages are frequently hosted at virtual private servers (VPSs) in the cloud networks of Alibaba and Tencent - hardly any surprise, given their disappointing botnet controller hosting track record.
Spamhaus is aware of similar campaigns targeting Taiwanese internet users.
Evolutionary pressure sparks evasion attempts
Given their demonstrated persistence and the resources at their disposal, Spamhaus assesses a lasting cease of China-nexus phishing operations targeting Japan as unlikely. Instead, recent developments suggest an uptick in abuse of Western cloud providers for disseminating phishing, while spam emissions from residential proxy networks continue unabated.
The latter currently accounts for approximately 66% of all the Exploits Blocklist (XBL) listings, and 37% of all the Combined Spam Sources (CSS) listings (3.34m and 1.73m, respectively), and China-nexus phishers are far from being the only threat actor leveraging residential proxies. Involved miscreants can be highly evasive, discarding specific residential proxies within minutes after their IPs are included in Spamhaus’s datasets.
Meanwhile, the phishing spam emissions from China Telecom and China Unicom continue, albeit at a reduced volume. We assess that this might be due to slow adoption of improved inbound spam filtering, such as Spamhaus ZEN, at Japanese email service providers (ESPs). Some of them even continue forwarding spam e-mails, and seem to be actively targeted by the threat actors to “wash” the phishing messages, thus increasing the miscreants’ deliverability rates.
Outlook and recommendations
While it remains unclear whether the threat actors involved will reemerge with yet another phish spam wave leveraging residential proxies, increased focus on abusing cloud hosting providers, or resort to other means, we anticipate the security threat they pose persists unabated. Shortcomings in phishing message quality (they never quite read the way a native speaker would phrase them) are counterbalanced by considerable emission volumes, persistence, as well as access to noteworthy financial and technical resources.
Having become en vogue amongst cybercriminals, residential proxy networks are increasingly coming under scrutiny by network operators, defenders and investigators. To combat security threats emanating from them, suggested countermeasures include:
- Awareness campaigns to educate users, abuse desks and IT (security) personnel about the risks of residential proxies, tolerating related devices or applications on their networks, and engaging with unsolicited or unexpected messages.
- Use of threat intelligence to identify and block malicious traffic before it can move into or out of your network, including non-SMTP traffic, and hunting for internal devices involved, as they may have been compromised.
- Blocking HELOs from non-existent, unresolvable, or invalid hostnames.
- Enforce on authentication metrics for email, in particular when operating e-mail forwarding infrastructure. Don’t become a spammers’ accomplice by blindly accepting and forwarding their messages!
- Identifying and disconnecting infected devices, particularly in corporate networks, given the security threats they pose. Spamhaus frequently observes residential proxies surfacing within critical infrastructure, including hospitals, governments and military networks.
- Sharing data and evidence with the companies being impersonated, enabling them to take action to protect their customers and reputation.
Sounds tedious? It is. Identifying and disconnecting one infected device in a corporate network can be a laborious, frustrating task, and is much more so when attempting to get a residential subscriber to do the same.
As they say, there is no glory in prevention. (After all, we should know.) However, every infected device removed from your network is one less ticking time bomb that may become the next “patient zero” in a potentially major security incident. Every spam message rejected at your perimeter saves computation and storage resources, and reduces the likelihood of end-users falling for miscreants’ nefarious attempts.
If you are a Computer Emergency Response Team (CERTs), please reach out to us - Spamhaus is happy to share data with you, including residential proxy activity in your constituency. If you are a postmaster, IT security employee or anti-abuse desk staff, ensure best practices and countermeasures outlined above are in place, to protect your networks and the internet as a whole. If you are a hosting provider, ensure you have a robust abuse prevention posture in place to thwart forthcoming attempts by miscreants to abuse your services. We are looking at major Western cloud providers in particular here - their networks might be the next primary vessel of China-nexus phish spammers.
Thank you all for your efforts!