blog
Botnet command & control domain registrations go through the roof in 2018
When Spamhaus Malware Labs observe a 40% increase in the number of domains that are being registered by cybercriminals to host a botnet command & control (C&C) it's time to understand where the threats are coming from in the top-level domains (TLDs) space and learn how you can protect against them.
In this Blog
Jump to
Introduction
When Spamhaus Malware Labs observe a 40% increase in the number of domains that are being registered by cybercriminals to host a botnet command & control (C&C) it’s time to stop. Take a look. And understand where the threats are coming from in the top-level domains (TLDs) space and learn how you can protect against them.
The importance of domain names
Cybercriminals prefer to use a domain name registered exclusively to host a botnet C&C. A dedicated domain name allows them to fire up a new virtual private server (VPS), load the botnet C&C kit, and immediately be back in contact with their botnet after their (former) hosting provider shuts down their botnet C&C server. Not having to change the configuration of each infected computer (bot) on the botnet is a significant advantage.
Number of botnet C&C domain names registered in 2018
Last year, compared to 2017, Spamhaus Malware Labs saw a 40% increase in the number of the domain names registered and set up by cybercriminals for the sole purpose of hosting a botnet C&C:
2017: 50,000 domains
2018: 69,961 domains*
Top-level domains – a brief overview
Before we get into the detail of which top-level domains were abused the most by botnet C&Cs in 2018 let’s take a look at some of the different types of top-level domains:
- Generic TLDs (gTLDs)- can be used by anyone
- Country code TLDs (ccTLDs)- some have restricted use within a particular country or region; however, others are licensed for general use which provides the same functionality of gTLDs
- Decentralized TLDs (dTLDs) -independent top-level domains that are not under the control of ICANN.
Most abused top-level domains in 2018
There were some interesting (and concerning) developments in this area, perhaps most notably was the rise of domain names registered to ‘.bit,’ a decentralized top-level domain (dTLD). Domain names with this type of TLD create additional issues when it comes to blocking malicious traffic and taking down these bad operators.
Top abused TLDs

Palau ‘.pw’ was the most abused TLD: The listings associated with ‘.pw’ rose by 56% in 2018, which was an additional 4,835 botnet C&Cs connected with this domain from the previous year.
Russia ‘.ru’ had a reduced number of domain registrations for botnet C&Cs: We noted a small decrease from 1,370 domain listings in 2017 to 1,183 in 2018. This saw ‘.ru’ ccTLD move out of the top ten rankings, down to #17.
Historically cybercriminals heavily abused ‘.ru’ & ‘.su’ ccTLDs, however, over recent years their operator has implemented measures which are having positive effects in reducing the amount of abuse across these 2 TLDs.
‘.tk,’ ‘.ml,’ ‘.ga,’ ‘.gg’ and ‘.cf’ made their first appearances in the Top 20: Originally ccTLDS; Freenom now operate them, and they are considered to be gTLDs. As the name implies “ËœFreenom’ provide domain names for free.
Given this business model, it’s not surprising that there has been a massive increase in abusive activity associated with them: Cybercriminals realize that their nefarious actions are likely to lead to their domain name being shut down, therefore prefer to obtain them for free rather than pay for them.
dTLD ‘.bit’ had an upsurge in listings: This dTLD didn’t make it into the ‘Top 20’ however we observed 108 domain names hosting botnet C&Cs with the dTLD ‘.bit.’ dTLDs provide criminals with advantages over other TLDs and consequently pose additional threats to users; therefore we feel it is necessary to highlight them:
- These domain names cannot be taken down or suspended when being used for malicious purposes, because there is no governing body associated with a dTLD.
- Researching malicious activity becomes more challenging as domain name registrations within dTLDs are usually entirely anonymous, with registrant information not being required.
- dTLDs bypass DNS Firewalls/Response Policy Zones (RPZ) that many ISPs and businesses use to protect their customers/users from cyber threats. They by-pass DNS Firewalls because dTLD domains are not resolvable through common DNS. Instead, they are resolved through nameservers that support ‘.bit,’ such as OpenNIC.
How can you protect against botnet C&C traffic on dTLD’s?
Border Gateway Protocol data feeds provide an added layer of protection. These feeds block connections to IPs involved in the most dangerous cybercrime and DDoS attacks via your edge router.
By taking just a few minutes to configure your edge router to peer with a Deteque BGP router and a null route, you can provide your network with up-to-date protection against botnets, alongside phishing and external attacks on your organization’s servers.
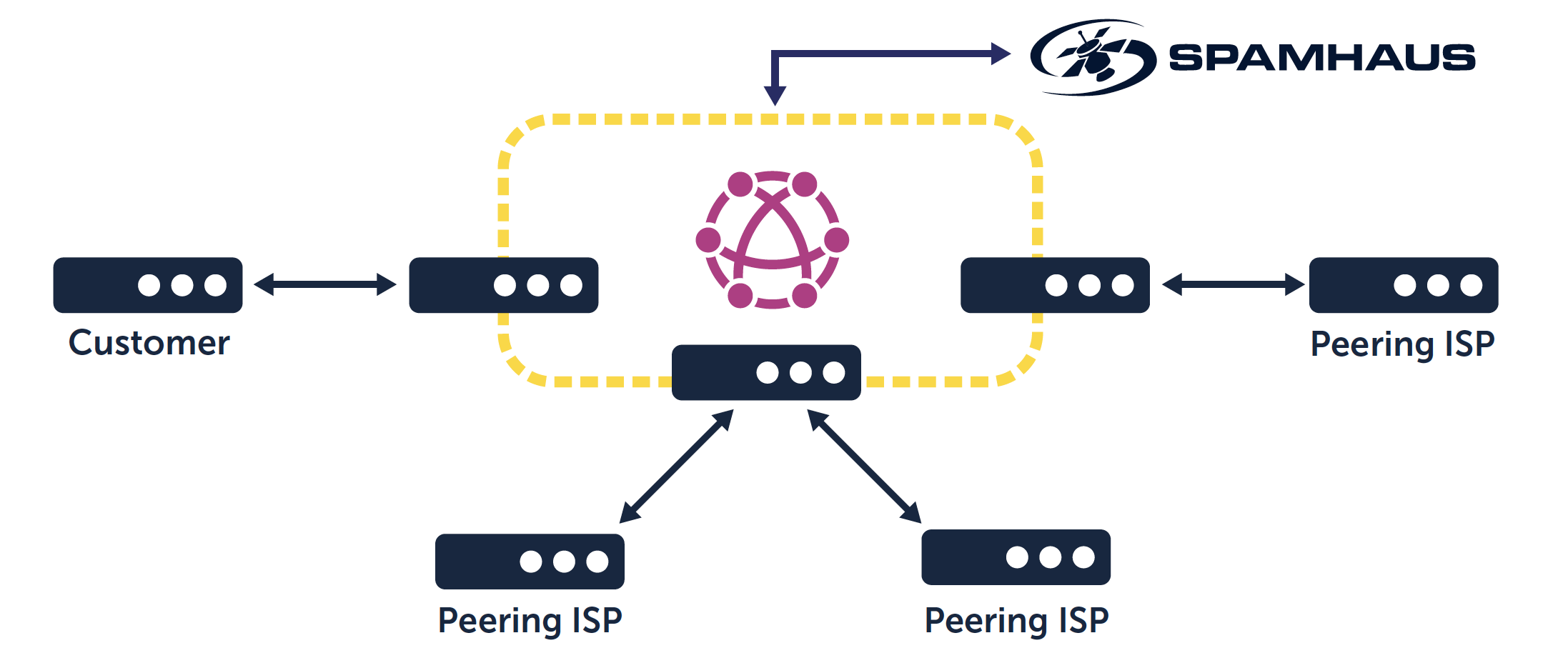
IT security has always required a multi-faceted approach, and with new threats continually coming to the fore, such as those posed by botnet C&C traffic registered to a dTLD, it is vital to continue to add layers of additional security.
*N.B. These numbers exclude hijacked domain names; domains owned by non-cybercriminals that were used without permission, and domains on ‘free sub-domain’ provider services.

