news
Emotet Email Aftermath
In this News Article
Jump to
Introduction
At the end of January 2021, Europol announced that a coordinated group of international authorities had taken control of the Emotet botnet infrastructure. Prior to this takedown, Emotet had spread itself using previously compromised email addresses to send tens of thousands of messages with malware-laden attachments using a technique called thread hijacking. Because of this method of proliferation, the takedown effort left a huge number of still-compromised email addresses vulnerable to further exploitation.
Emotet compromised accounts cleanup
Preventing these email addresses from potentially being abused by other malefactors was a necessary but complicated step. In mid-April, one of the law enforcement agencies involved in the takedown reached out to Spamhaus to ask if we could leverage our experience to help get the passwords for those email accounts changed.
We were provided with a list of approximately 1.3 million compromised email accounts, which we broke down into over 22,000 unique domains and roughly 3,000 responsible networks. To help these email providers, networks and their users/customers, we created a dedicated web page. It provides information about the Emotet botnet, the remediation process, and created a method of securely providing the necessary data to the correct network owners.
After having contacted everyone responsible and having provided additional support where needed we can safely say that currently over 60% of the compromised accounts have been secured. Spamhaus would like to thank the Abuse Desks, Trust & Safety departments and end users that took action - it really makes a difference! However, as we warned in a blog post published in January 2021, it is very important to recognize that this is not the end to the story.
The malware Emotet dropped remains a persistent and imminent threat
Six months after the Emotet takedown, a new picture is coming into focus. Emotet may be down, but the lucrative modus operandi of thread hijacking it popularized is being utilized by other ransomware botnets.
Many of these attacks commonly begin with a successful email phishing campaign, which installs a spam sending module, and then begins email thread hijacking: the insertion of poisoned emails into existing email threads with the intent of fooling recipients into opening them. Once a malware-laden attachment has been opened, the threat actors can perform thorough network reconnaissance and drop additional malware onto the compromised computer. This chain of events often leads to the most attention-grabbing threat of the moment: entire networks being hijacked by ransomware.
While there are different types of malware used to accomplish these attacks, we see that that variants previously dropped by Emotet are still very much alive: TrickBot steals access credentials for bank accounts, and is usually paired with the encryption trojan Ryuk - see below the graph for some examples of successful recent attacks.
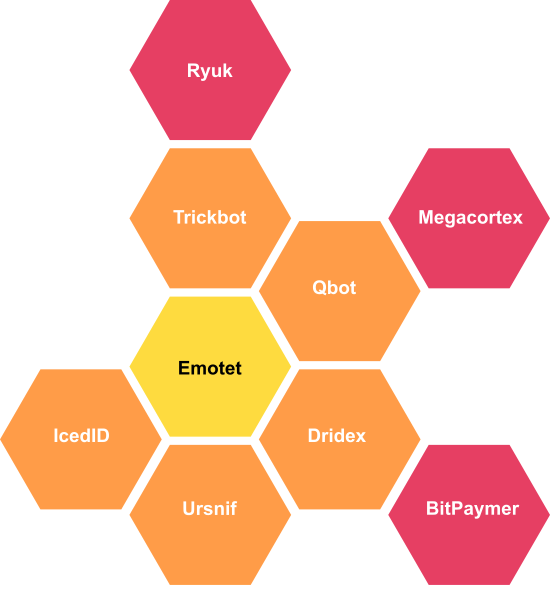
Ransomware post-Emotet
There has been an shift in attack type and frequency – criminals are moving from stealing data to actively disrupting operations. With this, the damages increase by orders of magnitude when the target is physical infrastructure or healthcare services. The following incidents illustrate that:
- On May 9, 2021, a Russian ransomware gang called DarkSide successfully encrypted the network of Colonial Pipeline, which supplies the American East Coast with nearly half of its gasoline and jet fuel, forcing them to shut down operations. The resulting panic and social disruption went on for days, spreading to states that were not materially affected at all.
- A few days earlier, the Norwegian energy technology company Volue was attacked resulting in the shutdown of water and water treatment facilities, affecting approximately 85% of the Norwegian population. (Attributed to Ryuk)
- In early June 2021, another ransomware attack forced Brazilian meat processing company JBS to close many of their beef plants, disrupting meat production in North America and Australia.
- Later in June 2021, another attack paralyzed Ireland's public health care system. In France, two hospitals had to divert ambulances, reschedule surgeries and to revert to using paper for patient records. (Attributed to Ryuk)
This approach has proven extremely effective as it provokes a very real sense of panic and urgency which creates an atmosphere most likely to lead to their desired result: a higher ransom can be demanded and the chance of it being paid increases.
Prevention beats remediation
Ransomware attacks are rapidly increasing in frequency and scope, with ever-larger ransom demands. They are now an established threat with vast implications which can often be prevented if the initial phishing campaign is unsuccessful. Practicing basic email and network security is your first line of defense.
Email security:
- Employee Education: The weakest link in network security is almost always people - social engineering is often key to a successful ransomware attack, which is why phishing emails are an easy path into an otherwise carefully secured system. Education is the first and most essential step every organisation should undertake. Teaching employees how to identify suspicious emails, and to not open unexpected attachments or unsolicited links can keep organisations from being compromised.
- Malware Scans: Reputable anti-malware scanners should be kept meticulously up to date and run on all devices at regularly scheduled and frequent intervals.
- Disable Macros: Not allowing macros in Microsoft Office to auto-run can prevent malware from executing in the event of a successful email thread hijack.
- Strong Passwords: Email accounts should have strong passwords to protect from bruteforce attacks.
- Rate Limits: Rate limiting outbound mail is an excellent way to slow a malware infection down. Very few individuals need to send significant volumes of email at a time! If network monitoring shows a sudden uptick in outbound mail volume, this should be considered an alarm.
- Watch Your Email Logs: Monitor SMTP server logs for bounced email. Bounces can indicate that an antispam block list such as Spamhaus has included your email server IP address. If a system is compromised, being unable to send email due to a spam related blocklisting can be an early warning signal that something bigger is happening.
Network security:
The United States CISA published a comprehensive overview of preventative network security measures and countermeasures that can be utilised in the event of a breach.
If you discover that any of your IP addresses are listed by Spamhaus, pay attention to the information provided when you look up the IP address on our checker tool. In most cases we have detailed information that will help you remediate the problem.
Malware is insidious, and it often relies on expert social engineering coupled with the human tendency to inertia: we don't take things very seriously until they directly affect us, and then it is often too late. These kinds of attacks are a threat to all of us, and should be treated with immediate urgency by all network operators, large and small. In an increasingly interconnected world linked by ever changing technology, adaptable security measures for networks and email systems MUST be kept up to date and enforced. We are all in this together; let's work to keep each other safe.
