blog
Some attack vectors Spamhaus is observing in early 2021
In this Blog
Jump to
Introduction
As we gallop apace into 2021, our researchers often get asked what the current trends and themes are they're seeing.
Compromised legitimate websites
Legitimate websites continue to be compromised in substantial numbers. We are still regularly seeing thousands and thousands of hacked WordPress sites. Once a cybercriminal has a website in their grubby hands, there are multiple ways (all bad) they will potentially use it. These can include; web shells, malware hosting, sending spam, hosting phishing websites, or redirector hosting. Often one website is used for several of these purposes!
As in most cases, prevention is better than cure, so we urge website owners to ensure they cover the basics:
- Ensure everyone who uses the website content management system (CMS), e.g., WordPress, uses log-in best practices, including 2-factor authentication.
- Always update to the latest version. These updates generally contain essential security patches; failure to update will leave your CMS open to abuse.
- Choose third party plugins carefully, and make sure they are also kept updated.
Residential proxies
This ongoing issue shows no sign of abating any time soon. Certain applications (most if not all from unofficial marketplaces) are downloaded to predominantly Android-based devices, including phones, tablets, digital media players, and streaming dongles.
As the saying goes, “There’s no such thing as a free lunch.” This is certainly true in this instance, as these applications which claim to be free are monetized via third party code. As you can imagine, this detail is buried deep within the application’s terms and conditions. The third party code allows miscreants to use the said device as a conduit for their nefarious actions.
These proxies are hard to find and hard to remove for the average victim. They open up many, many different abuse vectors. Spam is just one of them, but these are also used in large numbers for account creation, account takeover, stolen browser identities, and click/ad fraud.
Phish du jour
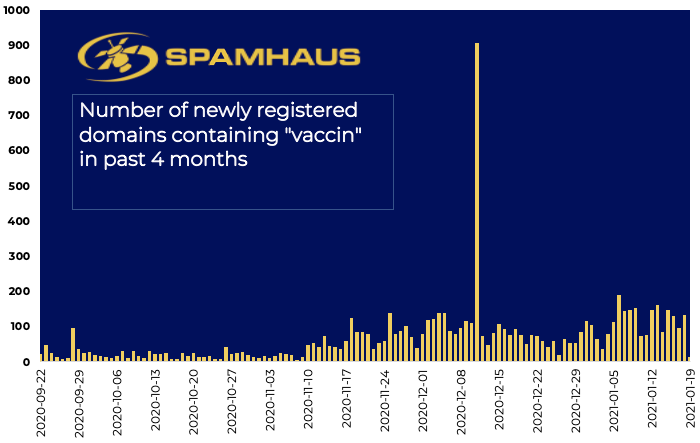
There is still a significant amount of phishing activity that leverages the news-of-the-day. After last year’s rush of covid related activity (see chart 1), we are now witnessing “vaccin" being used as the lure to interact (see chart 2).
Given the current state of the pandemic, this is obviously a powerful social engineering trick. We predict the use of “vaccination/vaccine” will escalate over the coming months. You only have to look at Chart #2 to see the upward trend over the past few months.
Chart 1: Domain registrations containing the word corona
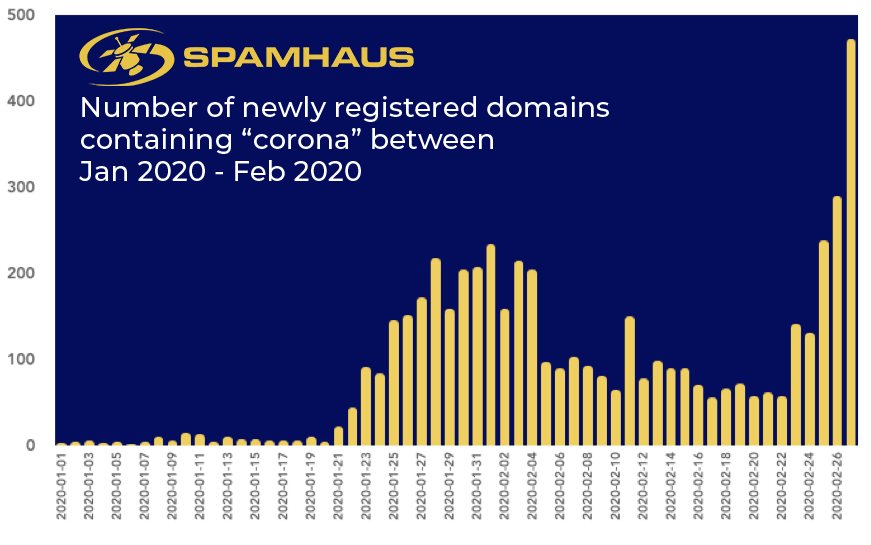
Chart 2: Domain registrations containing the word vaccin
Phishing with a different rod
More sophisticated bad actors will choose domains that are marginally different. You can already see this in some more traditional phishing campaigns that target the financial sector; instead of using domain names that include the phished brand's name, they use more generic or technical sounding domains.
These will often not get picked up by brand protection specialists. Additionally, it provides miscreants with the benefit of having a dedicated domain allowing the correct set-up of authentication, including SPF, DKIM, and DMARC, providing improved email deliverability.
Ransomware is still a lucrative business
When discussing ransomware, people usually think about poorly written emails sent en-masse by botnets. However, miscreants are becoming increasingly savvy in their approach.
While entry methods vary, we see far too many cases than necessary where compromise starts with an existing corporate account. For instance, the same password to the said account has been used across multiple website log-ins. One of these websites is compromised, and the log-in details are harvested before being made available on the dark web.
In addition to the above, we also see (semi) targeted phishing campaigns where cybercriminals carefully investigate their victims for weeks or months. Mechanisms for this kind of abuse often impersonate well-known business applications such as DocuSign or some of the file transfer services like Dropbox.
This story's moral is don’t reuse the same password across accounts and ensure log-in protocols are as secure as possible to prevent cybercriminals from impersonating the legitimate owner of the corporate account and always check the origination of documents.
Keep safe and secure
We hope you enjoyed our quick tour of current trends - we’ll keep you updated as 2021 progresses. Stay safe!