blog
Network Hijacking on the Rise
Introduction
As we discussed in a previous article, allocations of IP addresses (IPv4 addresses) are getting hard to come by, especially for spammers. Because the IP addresses they use quickly get a bad reputation as sources of spam, spammers constantly need fresh IPs that are not yet "burned".
To get around this problem, spammers increasingly now turn to a cheap and plentiful source of IP addresses by hijacking existing IP address ranges from under the noses of the legitimate owners and ARIN.
How is the hijacking accomplished? Let's take a look at one example.
Favourite targets for the hijackers are Legacy IP address ranges. Since these IP address ranges were originally issued prior to ARIN's inception in 1997, they can not be revoked for lack of paying yearly fees, and it's possible for them to lie dormant, sometimes forgotten by the legitimate owners.
In 2012, Spamhaus became aware of spam being sent from one of these legacy IP address ranges, 147.50.0.0/16, owned by Chemstress Consultant Company. Looking at the routing history for 147.50.0.0/16:
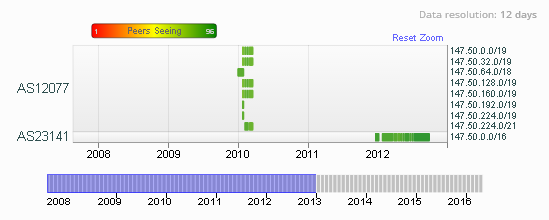
We can see that this range has not been used for a while, and has a history of short lived announcements. This isn't looking good for the announcements being legitimate.
So we can then take a look at the WHOIS history from ARIN and GoDaddy and trace the hijacker's exact steps:
1991-07-01 - ARIN record for Chemstress Consultant Company created (definitely a legacy range in 1991)
2011-08-19 - The domain CHEMSTRESSCONSULTING.COM is registered to "Timothy Tausch", the name found from the original ARIN records from 20 years ago (note: the real company's domain is CHEMSTRESS.COM)
2011-12-12 - ARIN is tricked into updating Timothy Tausch's contact information to the email address ttausch@chemstressconsulting.com
2011-12-16 - 147.50.0.0/16 starts to be announced on behalf of the hijacker
2012-06-10 - The company's address in ARIN is updated to "3465 S. Arlington Rd." (a PO Box store in Akron, Ohio)
Adding up all the evidence, this strongly pointed to this being hijacked. So we contacted the Internet Service Provider (ISP) making the announcement for this range. They informed us that they had already shut things down due to non-payment. It turns out the credit card given by "Tim's" partner in California was no good. The ISP provided us with some emails from the "owner" of this range: